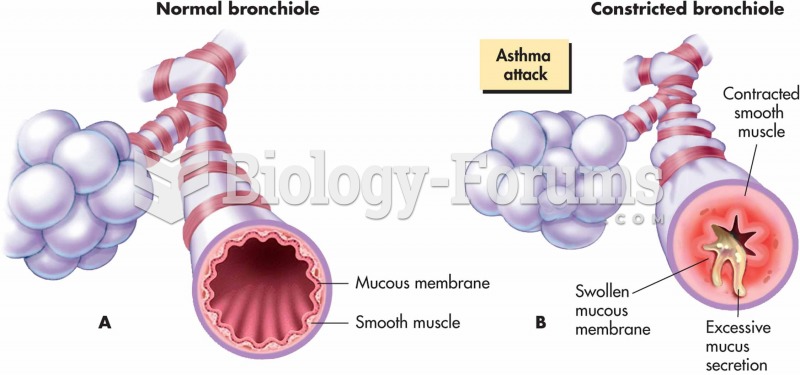
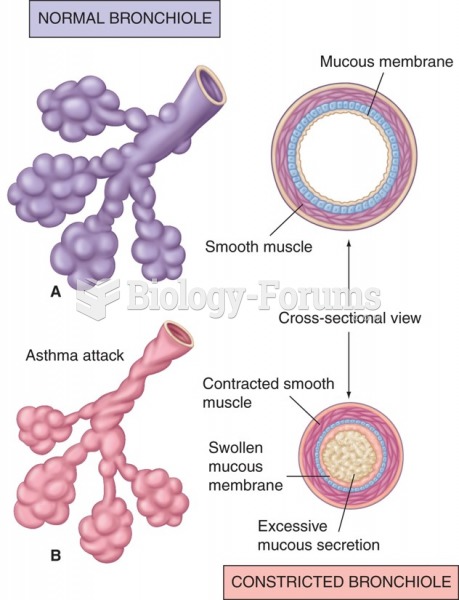
Answer to Question 1
Large criminal organizations can be highly efficient perpetrators of identity theft because they can exploit large amounts of personal information very quickly and efficiently. These organizations can use phishing attacks to gather personal information and then use it to perpetrate identity theft and other crimes. These criminal organizations often sell or trade information that they cannot use immediately to other organized crime entities around the world. Some of these criminal transactions are even conducted online. For example, a hacker who has planted zombie programs on a large number of computers (thus creating a zombie farm) might sell the right to use the zombie farm to an organized crime association that wants to launch a phishing attack (when a zombie farm is used this way, the attack is sometimes called a pharming attack). Individuals who commit these crimes have always posed a serious threat, but organized crimes entry into this activity increases the threat.
Answer to Question 2
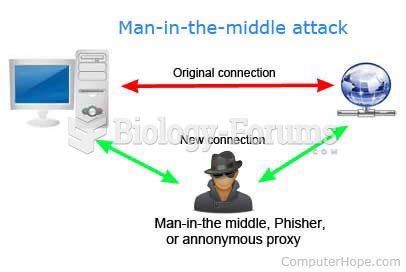
The basic structure of a phishing attack involves an attacker who sends e-mail messages to a large number of recipients who might have an account at a targeted Web site. The e-mail message tells the recipient that his or her account has been compromised and it is necessary for the recipient to log in to the account to correct the matter. The e-mail message includes a link that appears to be a link to the login page of the Web site. However, the link actually leads the recipient to the phishing attack perpetrators Web site, which is disguised to look like the targeted Web site. The unsuspecting recipient enters his or her login name and password, which the perpetrator captures and then uses to access the recipients account. Once inside the victims account, the perpetrator can access personal information, make purchases, or withdraw funds at will.
When the e-mails used in a phishing expedition are carefully designed to target a particular person or organization, the exploit is called spear phishing. The spear phishing perpetrator must do considerable research on the intended recipient, but by obtaining detailed personal information and using it in the e-mail, the perpetrator can greatly increase the chances that the victim will open the e-mail and click the link to the phishing Web site.
The basic structure of a phishing attack involves an attacker who sends e-mail messages to a large number of recipients who might have an account at a targeted Web site. The e-mail message tells the recipient that his or her account has been compromised and it is necessary for the recipient to log in to the account to correct the matter. The e-mail message includes a link that appears to be a link to the login page of the Web site. However, the link actually leads the recipient to the phishing attack perpetrators Web site, which is disguised to look like the targeted Web site. The unsuspecting recipient enters his or her login name and password, which the perpetrator captures and then uses to access the recipients account. Once inside the victims account, the perpetrator can access personal information, make purchases, or withdraw funds at will.
When the e-mails used in a phishing expedition are carefully designed to target a particular person or organization, the exploit is called spear phishing. The spear phishing perpetrator must do considerable research on the intended recipient, but by obtaining detailed personal information and using it in the e-mail, the perpetrator can greatly increase the chances that the victim will open the e-mail and click the link to the phishing Web site.