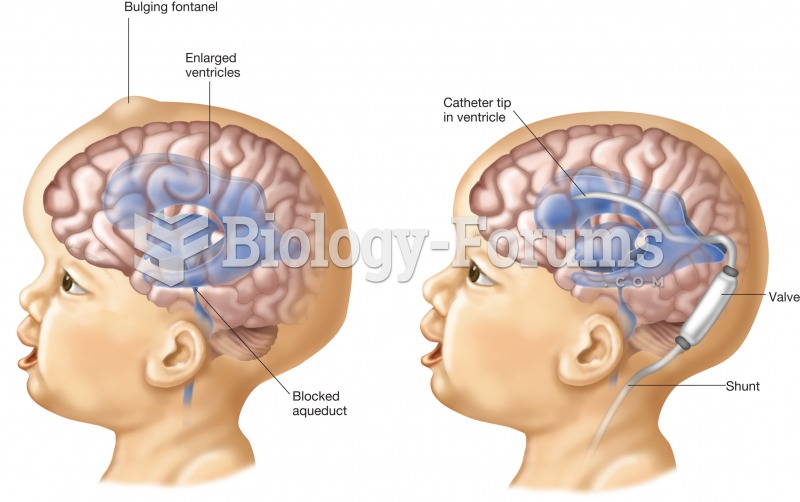
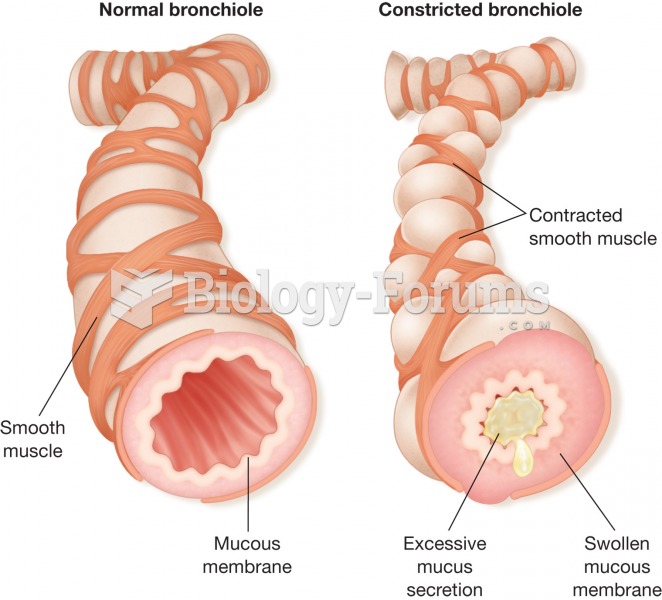
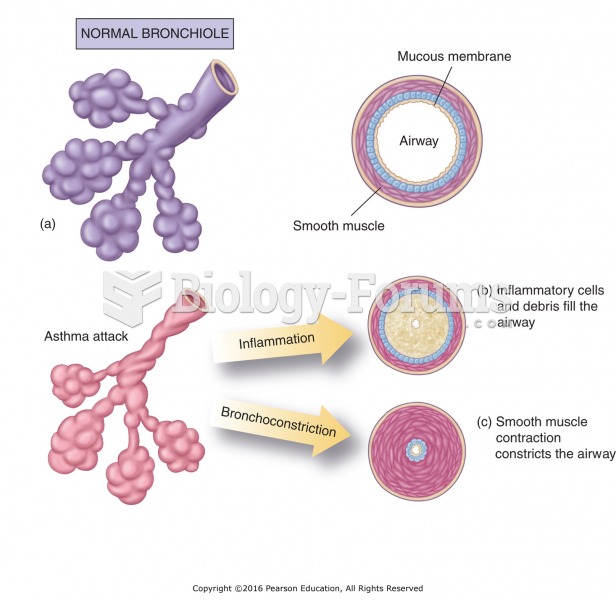
|
|
|
The effects of organophosphate poisoning are referred to by using the abbreviations “SLUD” or “SLUDGE,” It stands for: salivation, lacrimation, urination, defecation, GI upset, and emesis.
Adolescents often feel clumsy during puberty because during this time of development, their hands and feet grow faster than their arms and legs do. The body is therefore out of proportion. One out of five adolescents actually experiences growing pains during this period.
Coca-Cola originally used coca leaves and caffeine from the African kola nut. It was advertised as a therapeutic agent and "pickerupper." Eventually, its formulation was changed, and the coca leaves were removed because of the effects of regulation on cocaine-related products.
Human stomach acid is strong enough to dissolve small pieces of metal such as razor blades or staples.
Liver spots have nothing whatsoever to do with the liver. They are a type of freckles commonly seen in older adults who have been out in the sun without sufficient sunscreen.