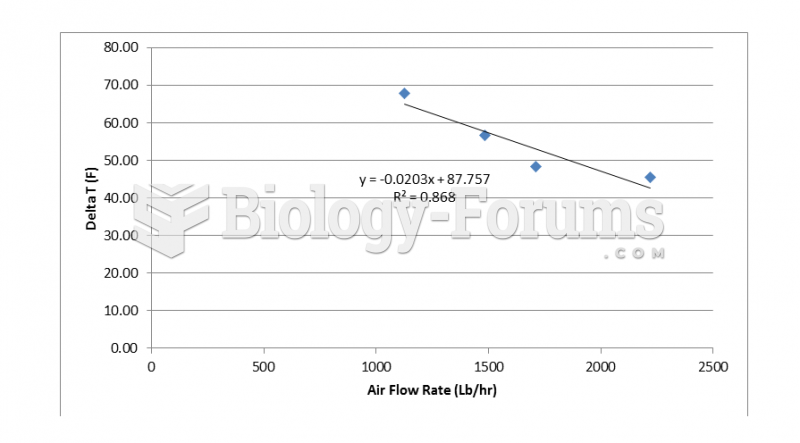
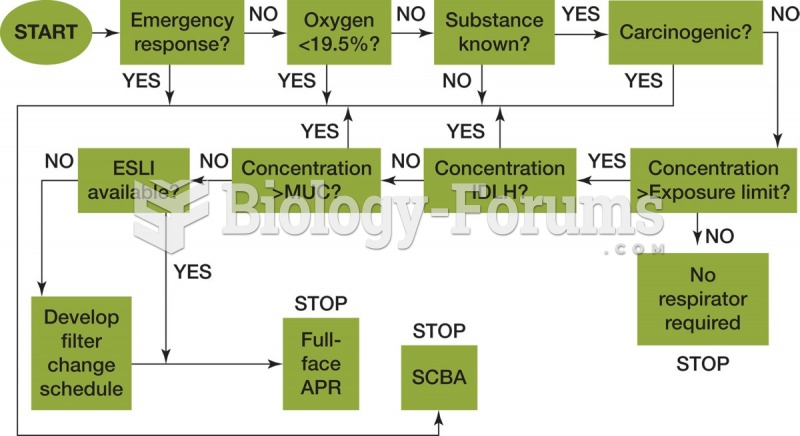
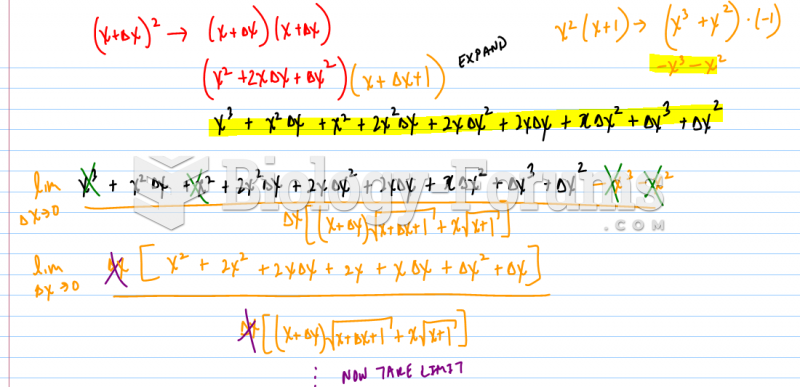|
|
|
Asthma is the most common chronic childhood disease in the world. Most children who develop asthma have symptoms before they are 5 years old.
Eating food that has been cooked with poppy seeds may cause you to fail a drug screening test, because the seeds contain enough opiate alkaloids to register as a positive.
In 1885, the Lloyd Manufacturing Company of Albany, New York, promoted and sold "Cocaine Toothache Drops" at 15 cents per bottle! In 1914, the Harrison Narcotic Act brought the sale and distribution of this drug under federal control.
Limit intake of red meat and dairy products made with whole milk. Choose skim milk, low-fat or fat-free dairy products. Limit fried food. Use healthy oils when cooking.
Coca-Cola originally used coca leaves and caffeine from the African kola nut. It was advertised as a therapeutic agent and "pickerupper." Eventually, its formulation was changed, and the coca leaves were removed because of the effects of regulation on cocaine-related products.
 The twin method can be used to investigate genetic and environmental influences on the development o
The twin method can be used to investigate genetic and environmental influences on the development o
 James A. Garfield lies mortally wounded. After failing to locate the bullet, surgeons called in Alex
James A. Garfield lies mortally wounded. After failing to locate the bullet, surgeons called in Alex