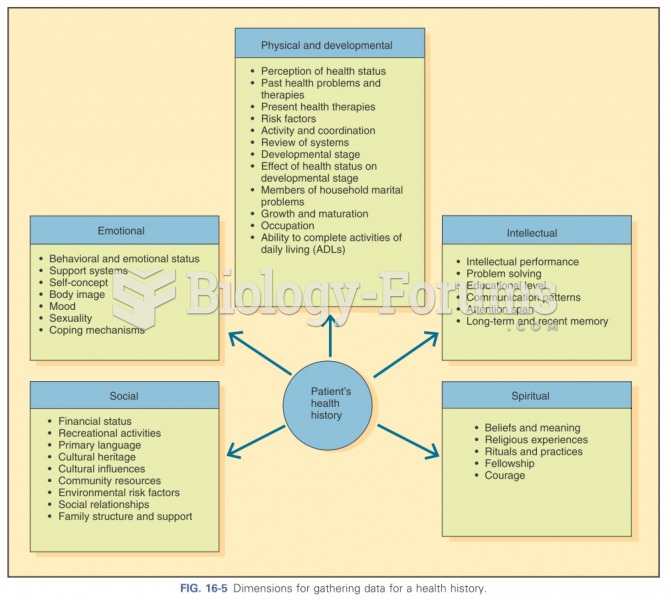
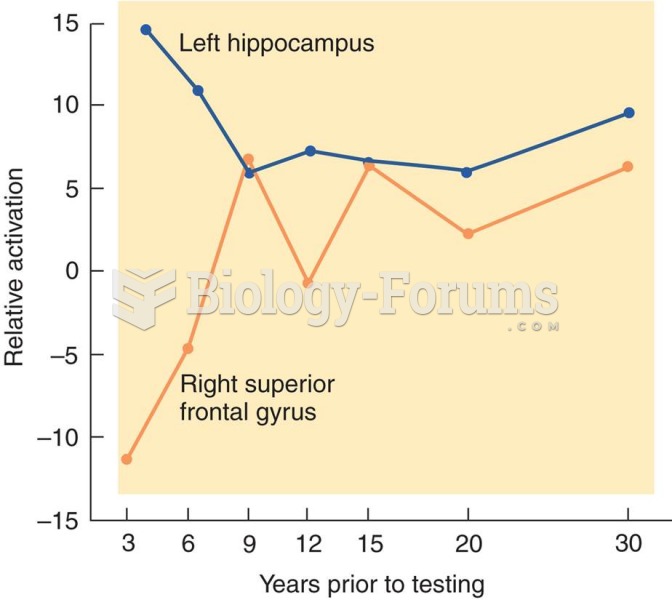
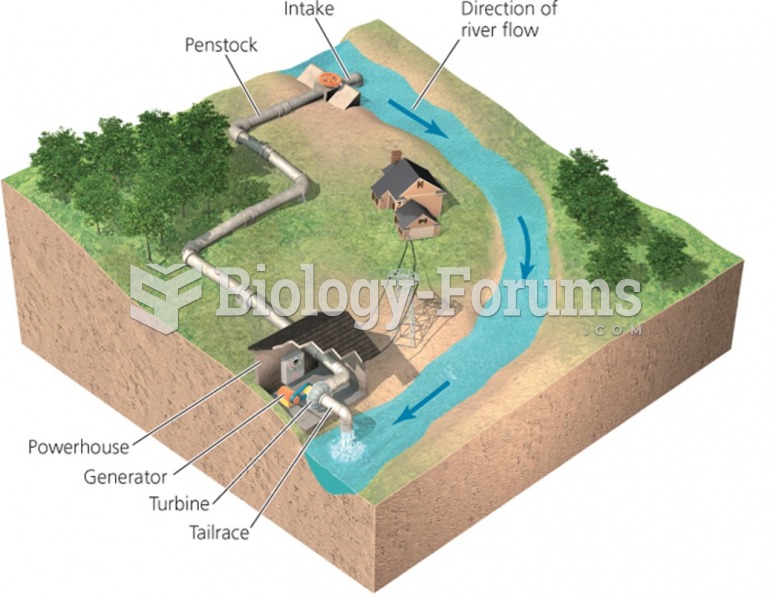
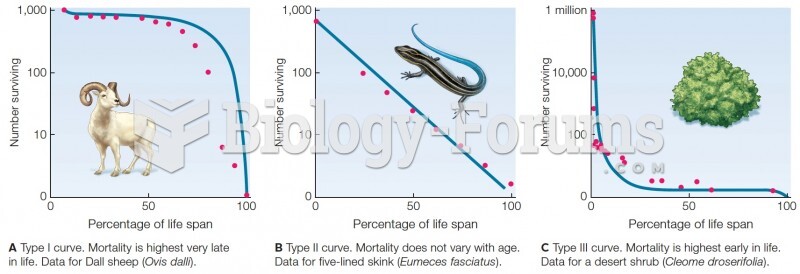
|
|
|
To maintain good kidney function, you should drink at least 3 quarts of water daily. Water dilutes urine and helps prevent concentrations of salts and minerals that can lead to kidney stone formation. Chronic dehydration is a major contributor to the development of kidney stones.
The eye muscles are the most active muscles in the whole body. The external muscles that move the eyes are the strongest muscles in the human body for the job they have to do. They are 100 times more powerful than they need to be.
The Romans did not use numerals to indicate fractions but instead used words to indicate parts of a whole.
All patients with hyperparathyroidism will develop osteoporosis. The parathyroid glands maintain blood calcium within the normal range. All patients with this disease will continue to lose calcium from their bones every day, and there is no way to prevent the development of osteoporosis as a result.
Sperm cells are so tiny that 400 to 500 million (400,000,000–500,000,000) of them fit onto 1 tsp.