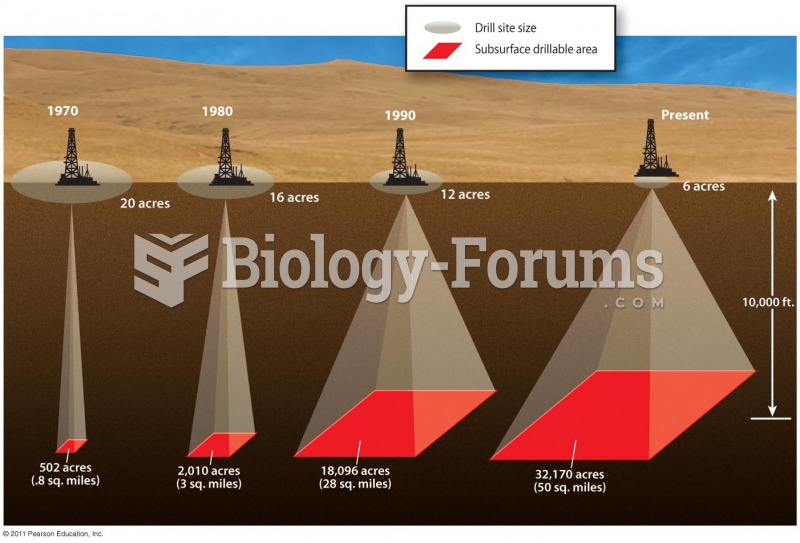
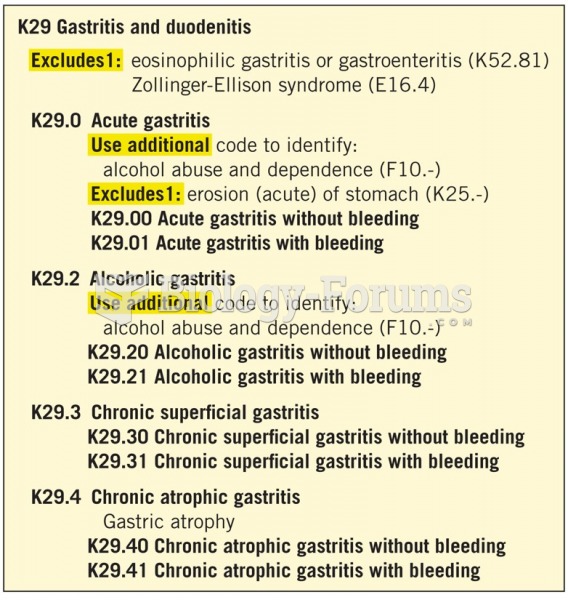
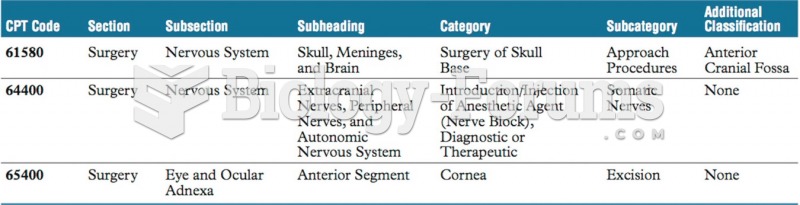
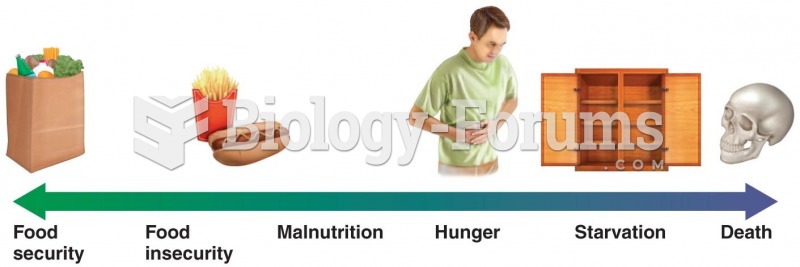
|
|
|
Lower drug doses for elderly patients should be used first, with titrations of the dose as tolerated to prevent unwanted drug-related pharmacodynamic effects.
To maintain good kidney function, you should drink at least 3 quarts of water daily. Water dilutes urine and helps prevent concentrations of salts and minerals that can lead to kidney stone formation. Chronic dehydration is a major contributor to the development of kidney stones.
About 600,000 particles of skin are shed every hour by each human. If you live to age 70 years, you have shed 105 pounds of dead skin.
On average, someone in the United States has a stroke about every 40 seconds. This is about 795,000 people per year.
About 80% of major fungal systemic infections are due to Candida albicans. Another form, Candida peritonitis, occurs most often in postoperative patients. A rare disease, Candida meningitis, may follow leukemia, kidney transplant, other immunosuppressed factors, or when suffering from Candida septicemia.