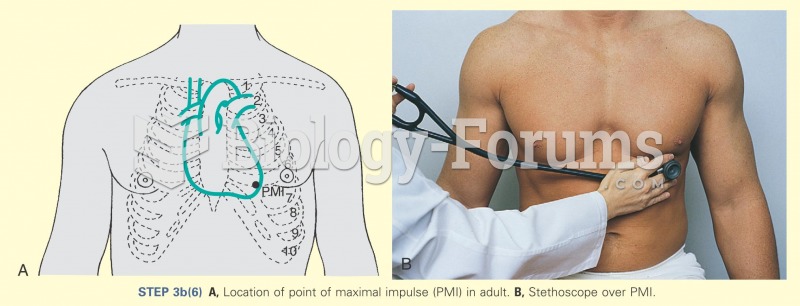
|
|
|
The most destructive flu epidemic of all times in recorded history occurred in 1918, with approximately 20 million deaths worldwide.
The most dangerous mercury compound, dimethyl mercury, is so toxic that even a few microliters spilled on the skin can cause death. Mercury has been shown to accumulate in higher amounts in the following types of fish than other types: swordfish, shark, mackerel, tilefish, crab, and tuna.
Immunoglobulin injections may give short-term protection against, or reduce severity of certain diseases. They help people who have an inherited problem making their own antibodies, or those who are having certain types of cancer treatments.
Acute bronchitis is an inflammation of the breathing tubes (bronchi), which causes increased mucus production and other changes. It is usually caused by bacteria or viruses, can be serious in people who have pulmonary or cardiac diseases, and can lead to pneumonia.
Vaccines cause herd immunity. If the majority of people in a community have been vaccinated against a disease, an unvaccinated person is less likely to get the disease since others are less likely to become sick from it and spread the disease.