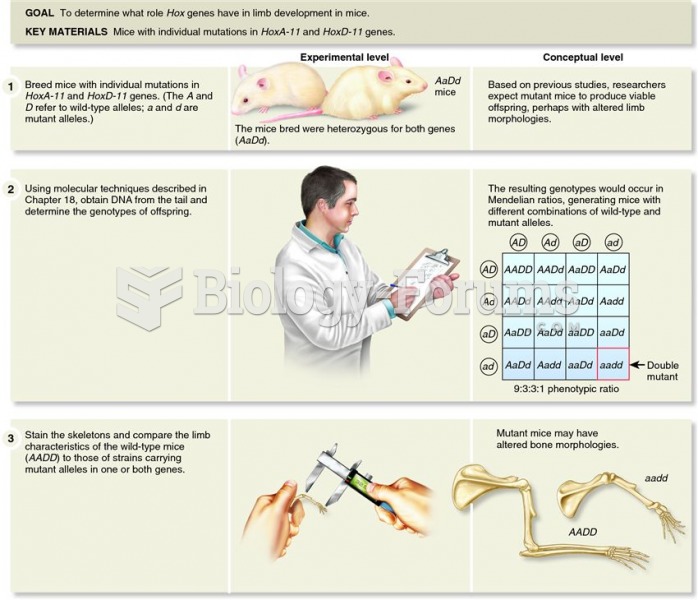
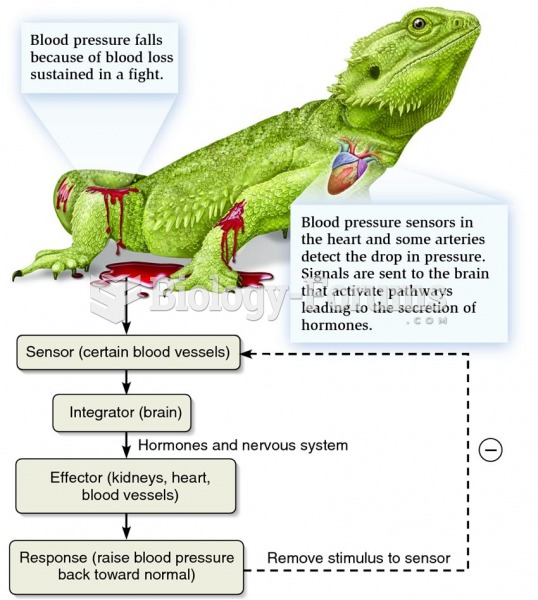
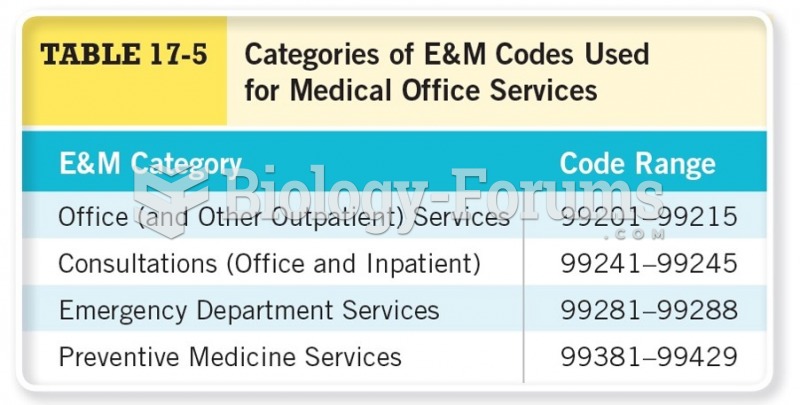
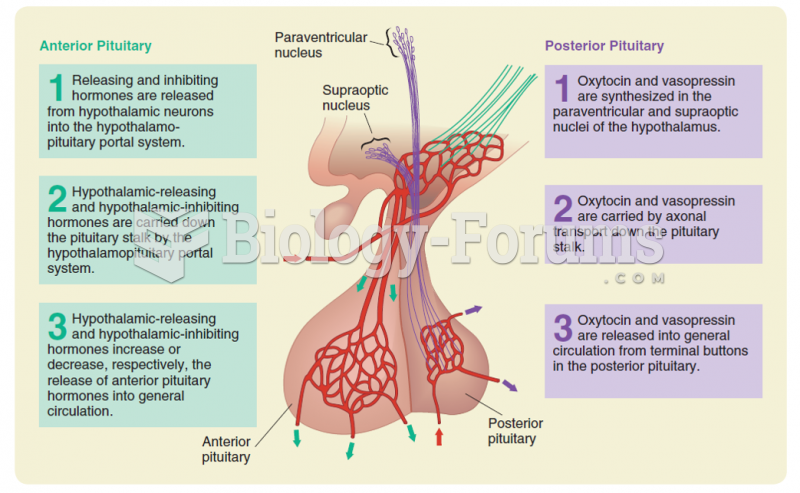
This topic contains a solution. Click here to go to the answer
|
|
|
Did you know?
Approximately one in three babies in the United States is now delivered by cesarean section. The number of cesarean sections in the United States has risen 46% since 1996.
Did you know?
The B-complex vitamins and vitamin C are not stored in the body and must be replaced each day.
Did you know?
On average, the stomach produces 2 L of hydrochloric acid per day.
Did you know?
Amphetamine poisoning can cause intravascular coagulation, circulatory collapse, rhabdomyolysis, ischemic colitis, acute psychosis, hyperthermia, respiratory distress syndrome, and pericarditis.
Did you know?
The first oral chemotherapy drug for colon cancer was approved by FDA in 2001.