|
|
|
Recent studies have shown that the number of medication errors increases in relation to the number of orders that are verified per pharmacist, per work shift.
The word drug comes from the Dutch word droog (meaning "dry"). For centuries, most drugs came from dried plants, hence the name.
Aspirin may benefit 11 different cancers, including those of the colon, pancreas, lungs, prostate, breasts, and leukemia.
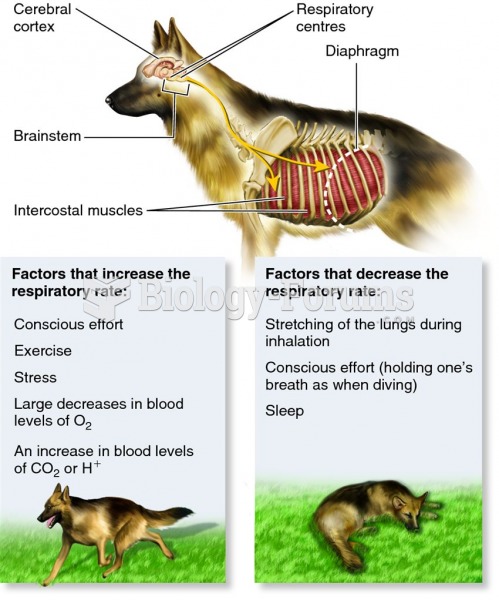
The effects of organophosphate poisoning are referred to by using the abbreviations “SLUD” or “SLUDGE,” It stands for: salivation, lacrimation, urination, defecation, GI upset, and emesis.
The human body's pharmacokinetics are quite varied. Our hair holds onto drugs longer than our urine, blood, or saliva. For example, alcohol can be detected in the hair for up to 90 days after it was consumed. The same is true for marijuana, cocaine, ecstasy, heroin, methamphetamine, and nicotine.