|
|
|
Patients who have been on total parenteral nutrition for more than a few days may need to have foods gradually reintroduced to give the digestive tract time to start working again.
Computer programs are available that crosscheck a new drug's possible trade name with all other trade names currently available. These programs detect dangerous similarities between names and alert the manufacturer of the drug.
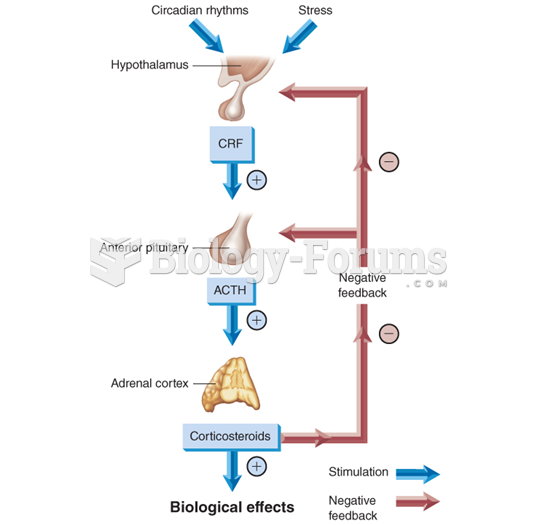
ACTH levels are normally highest in the early morning (between 6 and 8 A.M.) and lowest in the evening (between 6 and 11 P.M.). Therefore, a doctor who suspects abnormal levels looks for low ACTH in the morning and high ACTH in the evening.
The FDA recognizes 118 routes of administration.
Cyanide works by making the human body unable to use oxygen.