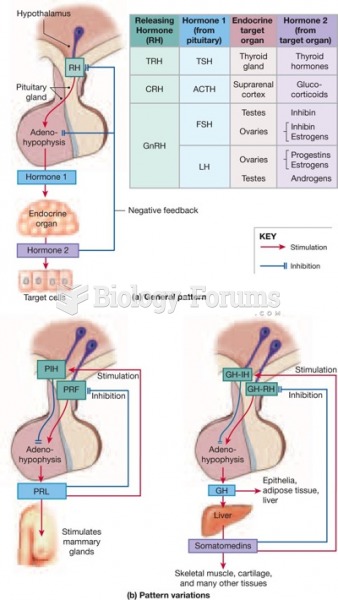
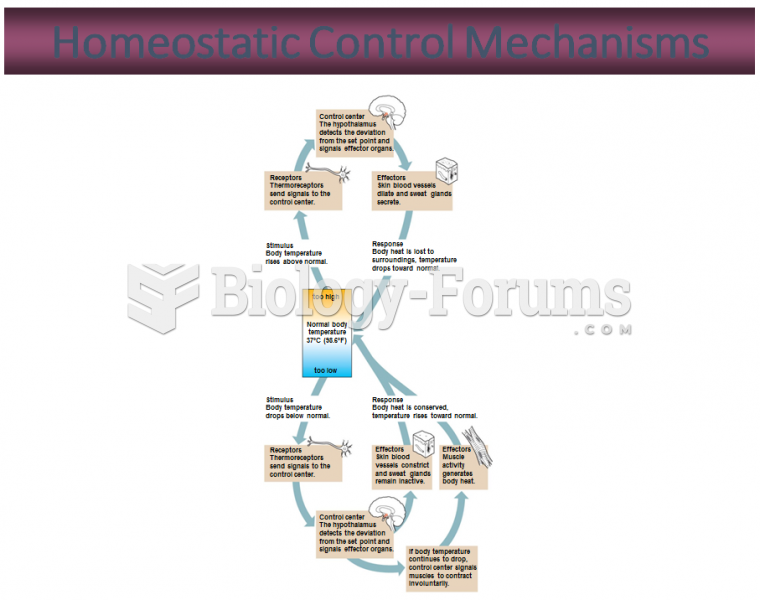
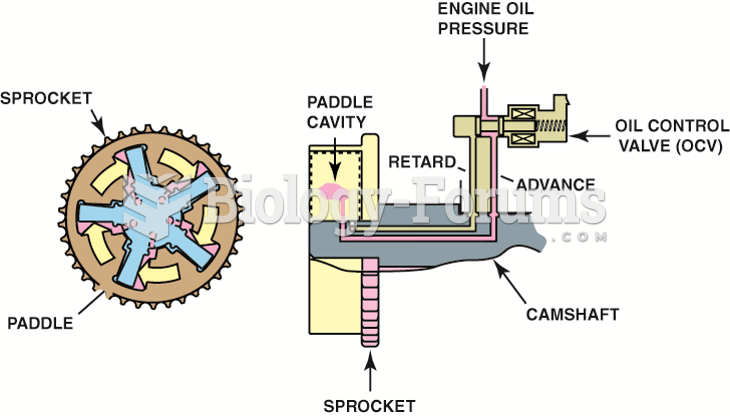
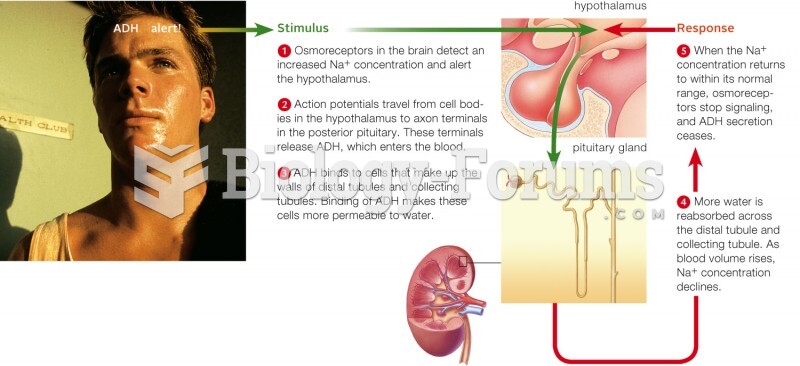
This topic contains a solution. Click here to go to the answer
|
|
|
Did you know?
Oliver Wendell Holmes is credited with introducing the words "anesthesia" and "anesthetic" into the English language in 1846.
Did you know?
Nearly all drugs pass into human breast milk. How often a drug is taken influences the amount of drug that will pass into the milk. Medications taken 30 to 60 minutes before breastfeeding are likely to be at peak blood levels when the baby is nursing.
Did you know?
In the United States, there is a birth every 8 seconds, according to the U.S. Census Bureau's Population Clock.
Did you know?
Stroke kills people from all ethnic backgrounds, but the people at highest risk for fatal strokes are: black men, black women, Asian men, white men, and white women.
Did you know?
Your heart beats over 36 million times a year.
 In 1885 masked Nebraskans seeking access to water posed for photographer S. D. Butcher, who captione
In 1885 masked Nebraskans seeking access to water posed for photographer S. D. Butcher, who captione
 One target for expanding medical services involves vaccinations. Only 78 percent of children ages 19 ...
One target for expanding medical services involves vaccinations. Only 78 percent of children ages 19 ...