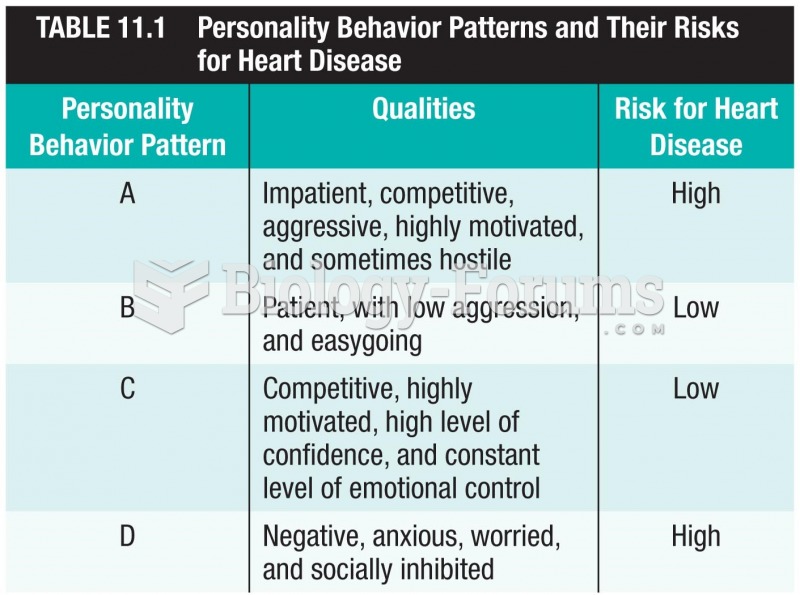
|
|
|
People with alcoholism are at a much greater risk of malnutrition than are other people and usually exhibit low levels of most vitamins (especially folic acid). This is because alcohol often takes the place of 50% of their daily intake of calories, with little nutritional value contained in it.
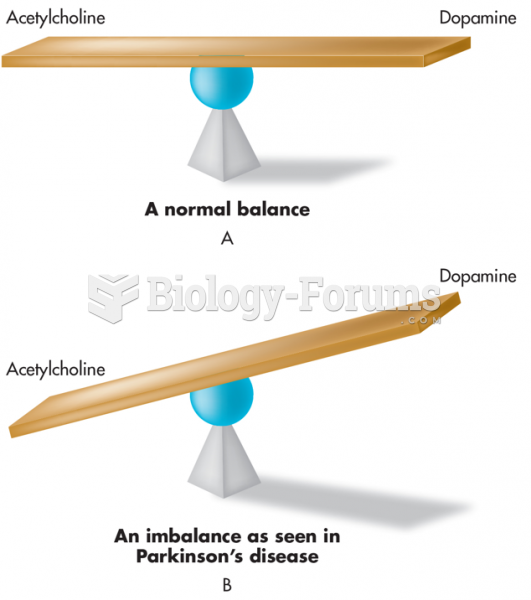
Parkinson's disease is both chronic and progressive. This means that it persists over a long period of time and that its symptoms grow worse over time.
About 600,000 particles of skin are shed every hour by each human. If you live to age 70 years, you have shed 105 pounds of dead skin.
Most strokes are caused when blood clots move to a blood vessel in the brain and block blood flow to that area. Thrombolytic therapy can be used to dissolve the clot quickly. If given within 3 hours of the first stroke symptoms, this therapy can help limit stroke damage and disability.
To maintain good kidney function, you should drink at least 3 quarts of water daily. Water dilutes urine and helps prevent concentrations of salts and minerals that can lead to kidney stone formation. Chronic dehydration is a major contributor to the development of kidney stones.
 Booker T. Washington in his office at Tuskegee Institute, 1900. Washington chose a policy of accommo
Booker T. Washington in his office at Tuskegee Institute, 1900. Washington chose a policy of accommo
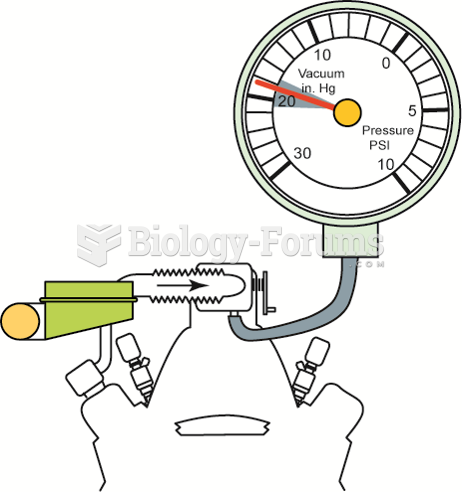 An engine in good mechanical condition should produce 17 to 21 inches Hg of vacuum at idle at sea ...
An engine in good mechanical condition should produce 17 to 21 inches Hg of vacuum at idle at sea ...