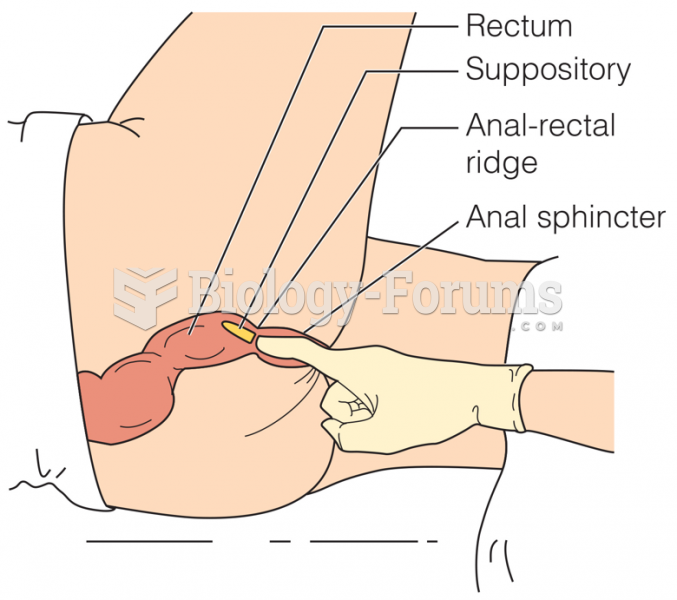
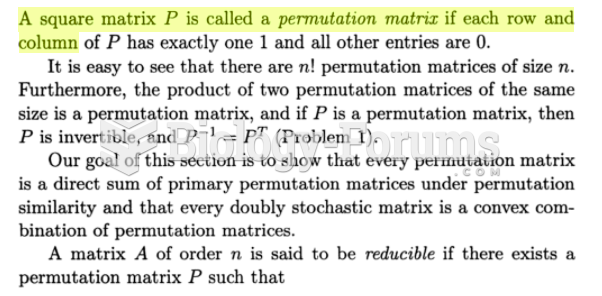
|
|
|
Every 10 seconds, a person in the United States goes to the emergency room complaining of head pain. About 1.2 million visits are for acute migraine attacks.
Cytomegalovirus affects nearly the same amount of newborns every year as Down syndrome.
Though “Krazy Glue” or “Super Glue” has the ability to seal small wounds, it is not recommended for this purpose since it contains many substances that should not enter the body through the skin, and may be harmful.
Between 1999 and 2012, American adults with high total cholesterol decreased from 18.3% to 12.9%
To prove that stomach ulcers were caused by bacteria and not by stress, a researcher consumed an entire laboratory beaker full of bacterial culture. After this, he did indeed develop stomach ulcers, and won the Nobel Prize for his discovery.
 Succession in the intertidal zone involves colonization and competition for limited space among spec
Succession in the intertidal zone involves colonization and competition for limited space among spec
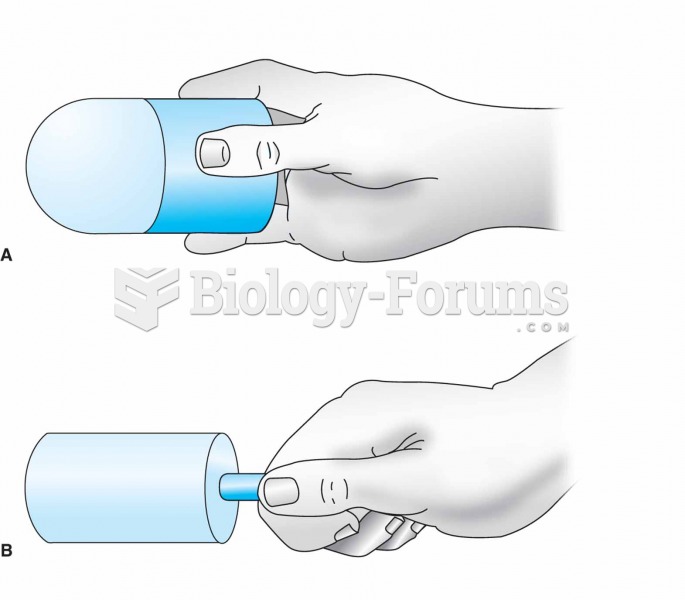 For ice massage, ice is frozen in a cylindrical container or a paper cup (A). The top half of the cu
For ice massage, ice is frozen in a cylindrical container or a paper cup (A). The top half of the cu