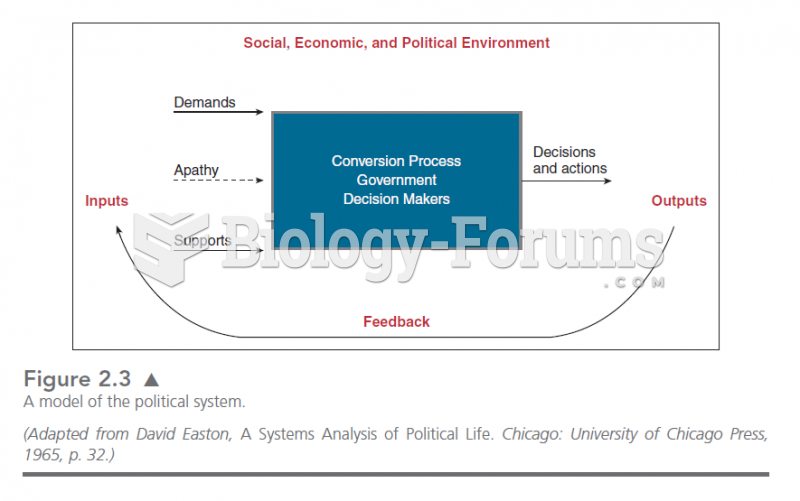
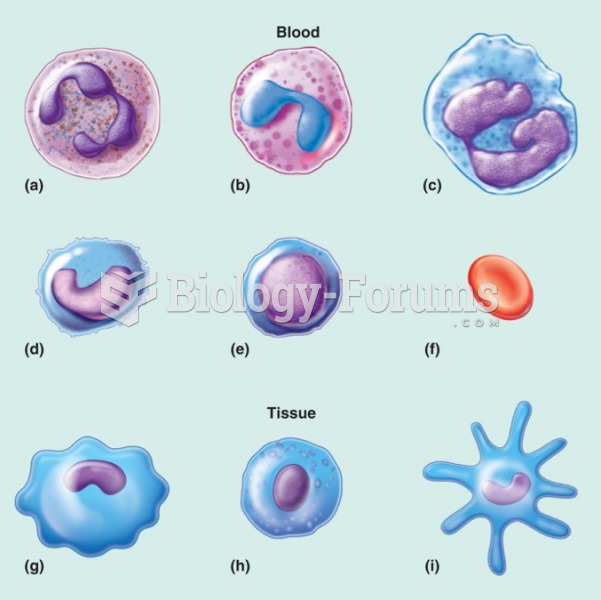
|
|
|
Asthma attacks and symptoms usually get started by specific triggers (such as viruses, allergies, gases, and air particles). You should talk to your doctor about these triggers and find ways to avoid or get rid of them.
Patients should never assume they are being given the appropriate drugs. They should make sure they know which drugs are being prescribed, and always double-check that the drugs received match the prescription.
Ether was used widely for surgeries but became less popular because of its flammability and its tendency to cause vomiting. In England, it was quickly replaced by chloroform, but this agent caused many deaths and lost popularity.
The strongest synthetic topical retinoid drug available, tazarotene, is used to treat sun-damaged skin, acne, and psoriasis.
If you use artificial sweeteners, such as cyclamates, your eyes may be more sensitive to light. Other factors that will make your eyes more sensitive to light include use of antibiotics, oral contraceptives, hypertension medications, diuretics, and antidiabetic medications.