|
|
|
The use of salicylates dates back 2,500 years to Hippocrates’s recommendation of willow bark (from which a salicylate is derived) as an aid to the pains of childbirth. However, overdosage of salicylates can harm body fluids, electrolytes, the CNS, the GI tract, the ears, the lungs, the blood, the liver, and the kidneys and cause coma or death.
The National Institutes of Health have supported research into acupuncture. This has shown that acupuncture significantly reduced pain associated with osteoarthritis of the knee, when used as a complement to conventional therapies.
Alcohol acts as a diuretic. Eight ounces of water is needed to metabolize just 1 ounce of alcohol.
The people with the highest levels of LDL are Mexican American males and non-Hispanic black females.
Everyone has one nostril that is larger than the other.
 A client is having an endoscopy performed by a physician who views the upper gastrointestinal intern
A client is having an endoscopy performed by a physician who views the upper gastrointestinal intern
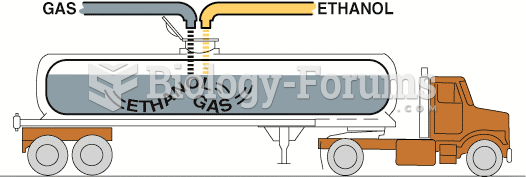 Sequential blending uses a computer to calculate the correct ratio as well as the prescribed order ...
Sequential blending uses a computer to calculate the correct ratio as well as the prescribed order ...