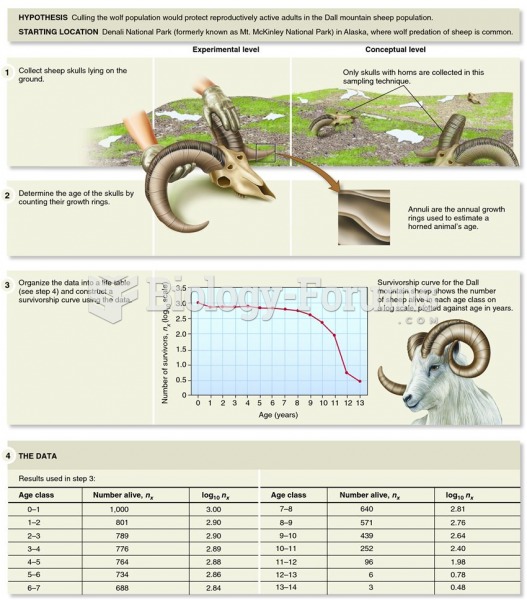
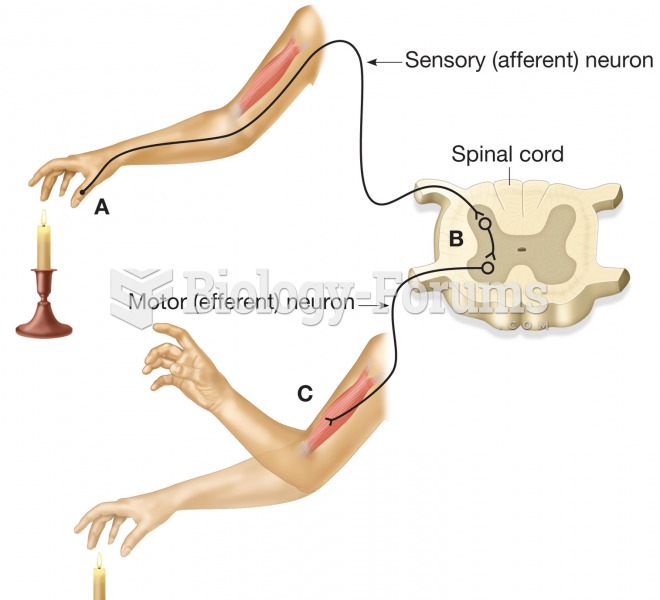
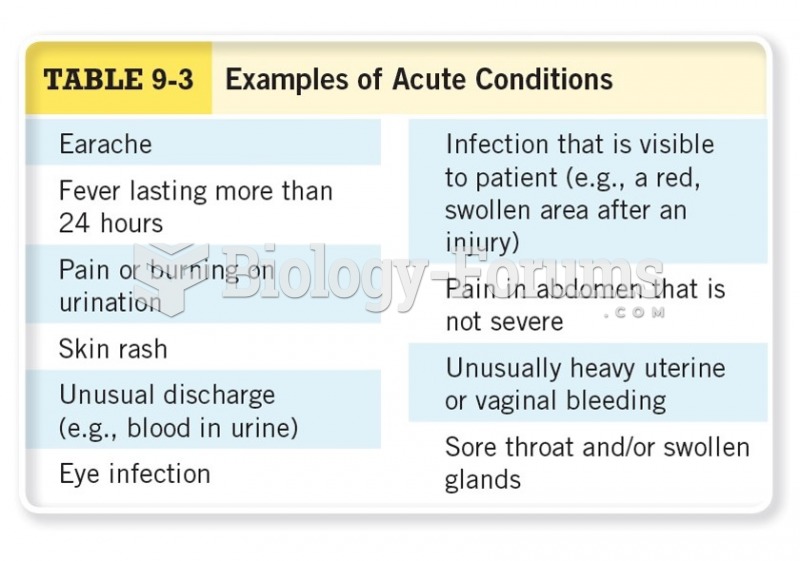
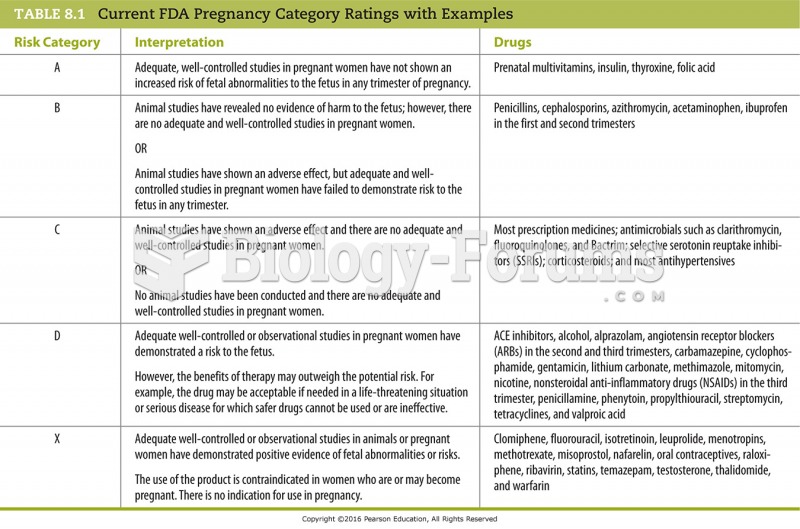
|
|
|
Asthma occurs in one in 11 children and in one in 12 adults. African Americans and Latinos have a higher risk for developing asthma than other groups.
Bacteria have flourished on the earth for over three billion years. They were the first life forms on the planet.
Side effects from substance abuse include nausea, dehydration, reduced productivitiy, and dependence. Though these effects usually worsen over time, the constant need for the substance often overcomes rational thinking.
There are 60,000 miles of blood vessels in every adult human.
In inpatient settings, adverse drug events account for an estimated one in three of all hospital adverse events. They affect approximately 2 million hospital stays every year, and prolong hospital stays by between one and five days.