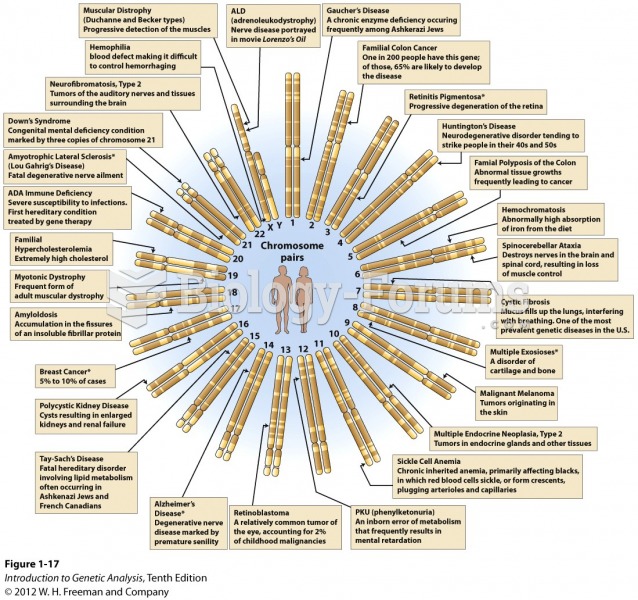
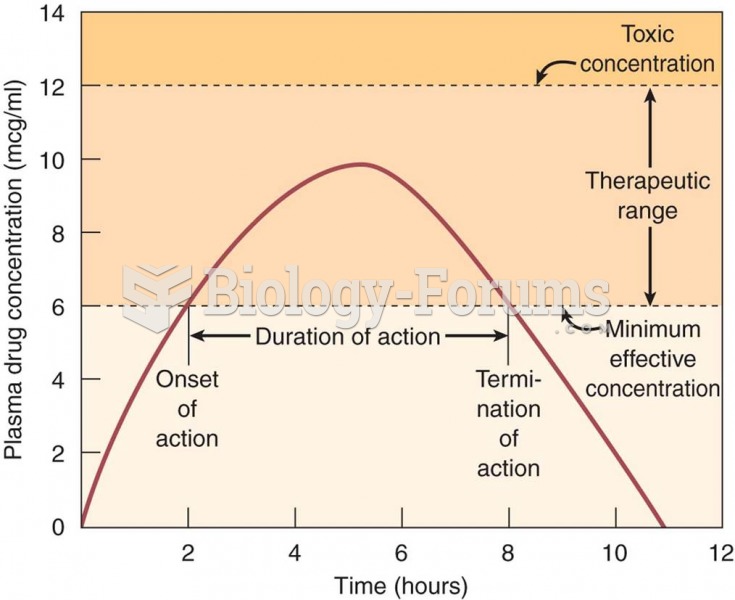
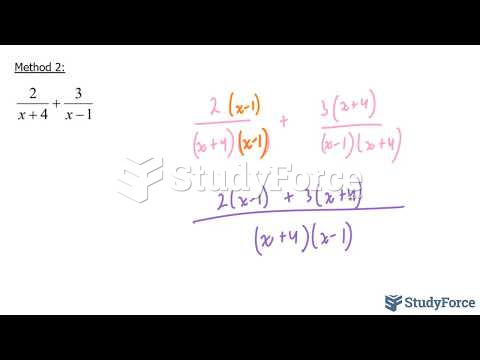
|
|
|
It is important to read food labels and choose foods with low cholesterol and saturated trans fat. You should limit saturated fat to no higher than 6% of daily calories.
A serious new warning has been established for pregnant women against taking ACE inhibitors during pregnancy. In the study, the risk of major birth defects in children whose mothers took ACE inhibitors during the first trimester was nearly three times higher than in children whose mothers didn't take ACE inhibitors. Physicians can prescribe alternative medications for pregnant women who have symptoms of high blood pressure.
Although not all of the following muscle groups are commonly used, intramuscular injections may be given into the abdominals, biceps, calves, deltoids, gluteals, laterals, pectorals, quadriceps, trapezoids, and triceps.
Intradermal injections are somewhat difficult to correctly administer because the skin layers are so thin that it is easy to accidentally punch through to the deeper subcutaneous layer.
Computer programs are available that crosscheck a new drug's possible trade name with all other trade names currently available. These programs detect dangerous similarities between names and alert the manufacturer of the drug.