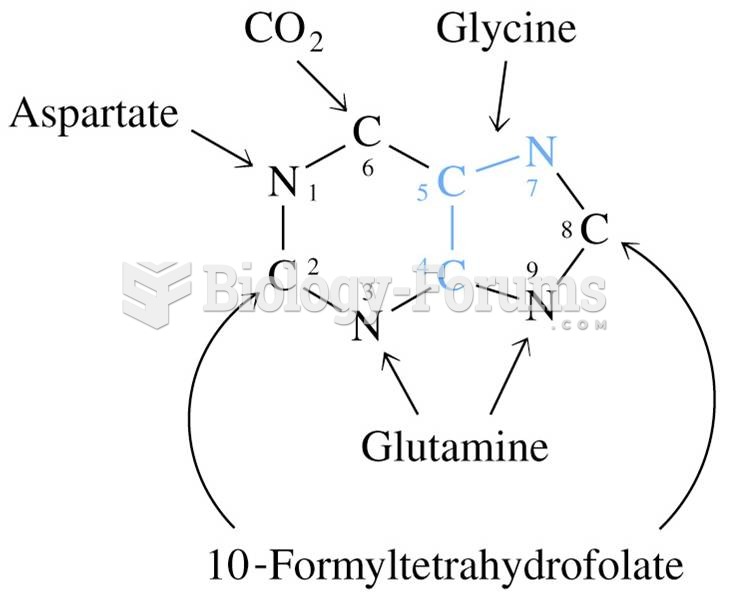
|
|
|
Cytomegalovirus affects nearly the same amount of newborns every year as Down syndrome.
The liver is the only organ that has the ability to regenerate itself after certain types of damage. As much as 25% of the liver can be removed, and it will still regenerate back to its original shape and size. However, the liver cannot regenerate after severe damage caused by alcohol.
To prove that stomach ulcers were caused by bacteria and not by stress, a researcher consumed an entire laboratory beaker full of bacterial culture. After this, he did indeed develop stomach ulcers, and won the Nobel Prize for his discovery.
Signs of depression include feeling sad most of the time for 2 weeks or longer; loss of interest in things normally enjoyed; lack of energy; sleep and appetite disturbances; weight changes; feelings of hopelessness, helplessness, or worthlessness; an inability to make decisions; and thoughts of death and suicide.
It is widely believed that giving a daily oral dose of aspirin to heart attack patients improves their chances of survival because the aspirin blocks the formation of new blood clots.