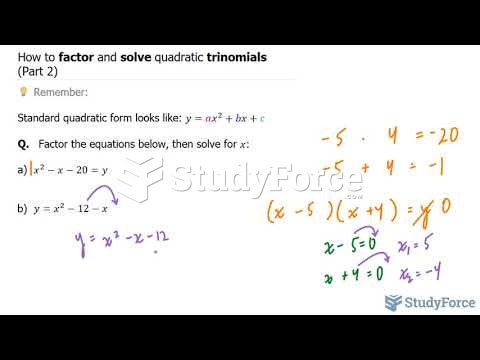
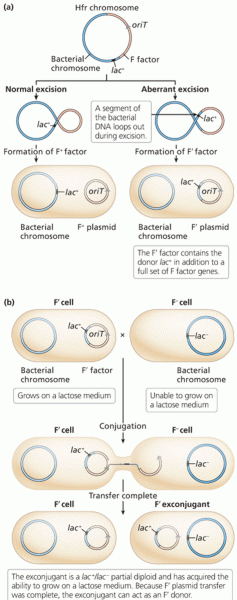
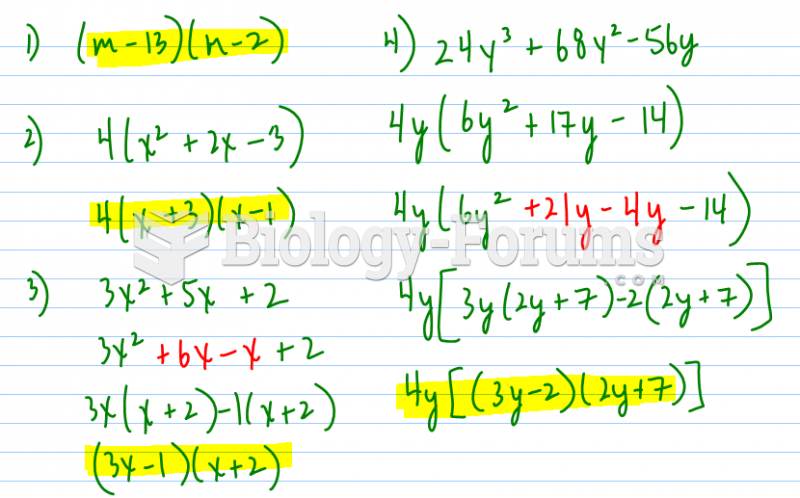|
|
|
The liver is the only organ that has the ability to regenerate itself after certain types of damage. As much as 25% of the liver can be removed, and it will still regenerate back to its original shape and size. However, the liver cannot regenerate after severe damage caused by alcohol.
In the ancient and medieval periods, dysentery killed about ? of all babies before they reach 12 months of age. The disease was transferred through contaminated drinking water, because there was no way to adequately dispose of sewage, which contaminated the water.
The most common treatment options for addiction include psychotherapy, support groups, and individual counseling.
Lower drug doses for elderly patients should be used first, with titrations of the dose as tolerated to prevent unwanted drug-related pharmacodynamic effects.
The first war in which wide-scale use of anesthetics occurred was the Civil War, and 80% of all wounds were in the extremities.