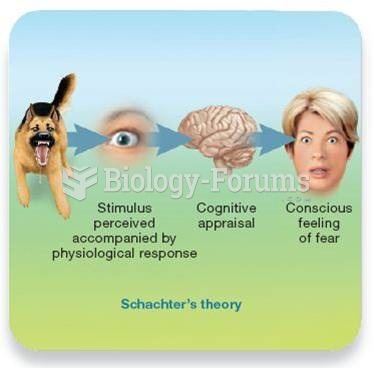
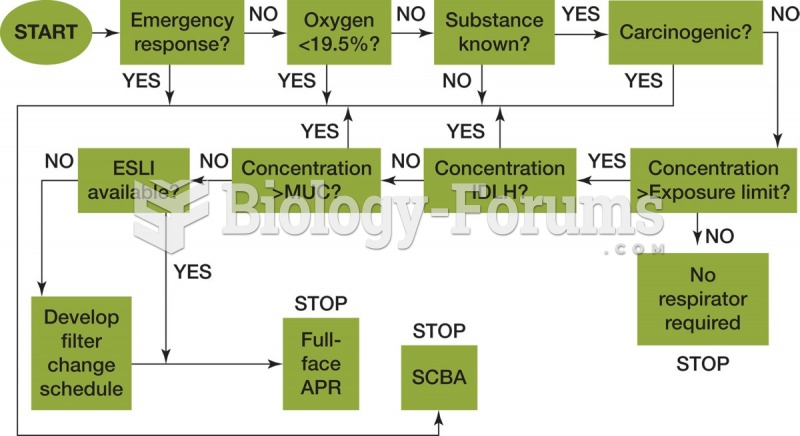
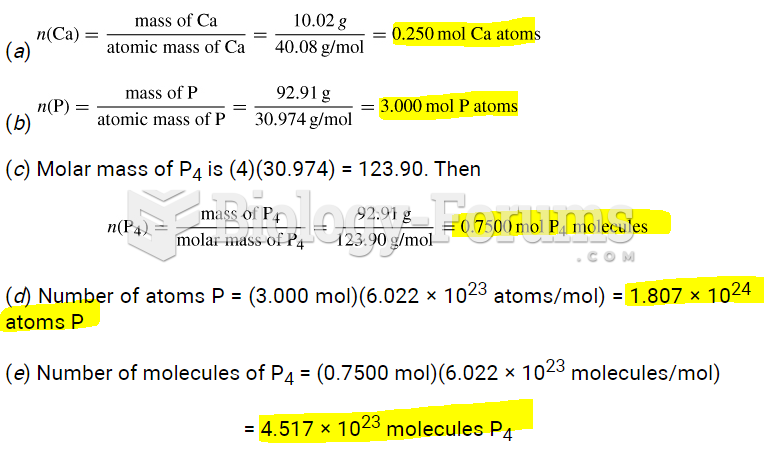
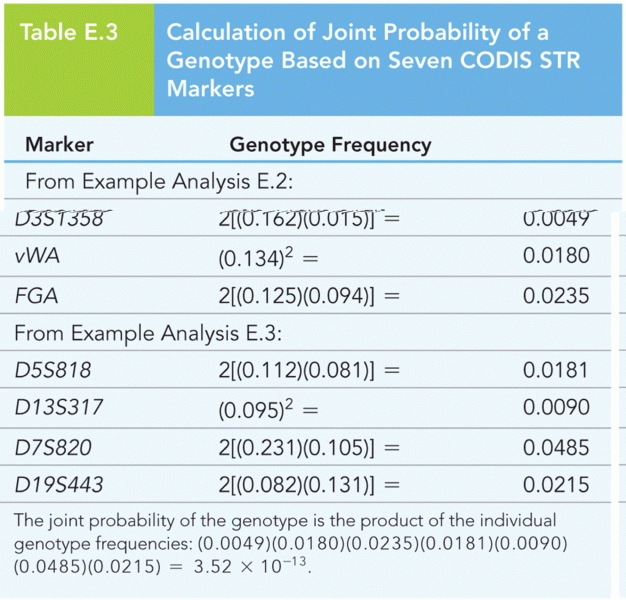
|
|
|
Throughout history, plants containing cardiac steroids have been used as heart drugs and as poisons (e.g., in arrows used in combat), emetics, and diuretics.
For about 100 years, scientists thought that peptic ulcers were caused by stress, spicy food, and alcohol. Later, researchers added stomach acid to the list of causes and began treating ulcers with antacids. Now it is known that peptic ulcers are predominantly caused by Helicobacter pylori, a spiral-shaped bacterium that normally exist in the stomach.
All adults should have their cholesterol levels checked once every 5 years. During 2009–2010, 69.4% of Americans age 20 and older reported having their cholesterol checked within the last five years.
Vital signs (blood pressure, temperature, pulse rate, respiration rate) should be taken before any drug administration. Patients should be informed not to use tobacco or caffeine at least 30 minutes before their appointment.
The effects of organophosphate poisoning are referred to by using the abbreviations “SLUD” or “SLUDGE,” It stands for: salivation, lacrimation, urination, defecation, GI upset, and emesis.
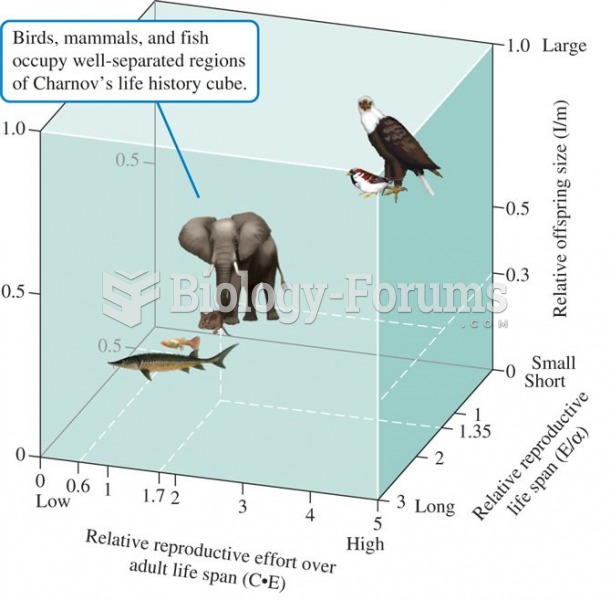 Life-history cube, a classification of fish, mammals, and altricial birds based on three dimensionle
Life-history cube, a classification of fish, mammals, and altricial birds based on three dimensionle
 Hospice care is based on the belief that when death is inevitable, professional caregivers should ...
Hospice care is based on the belief that when death is inevitable, professional caregivers should ...