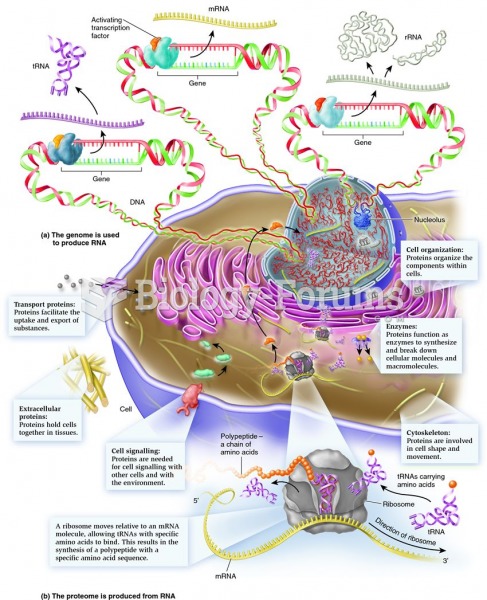
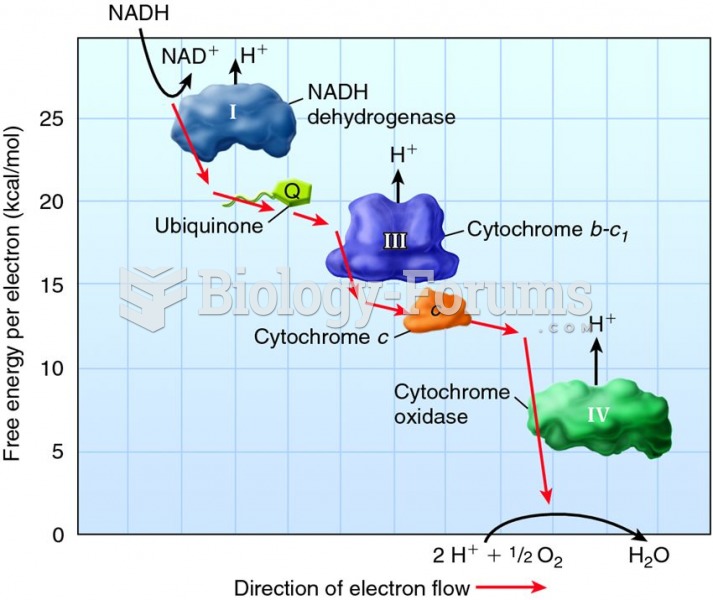
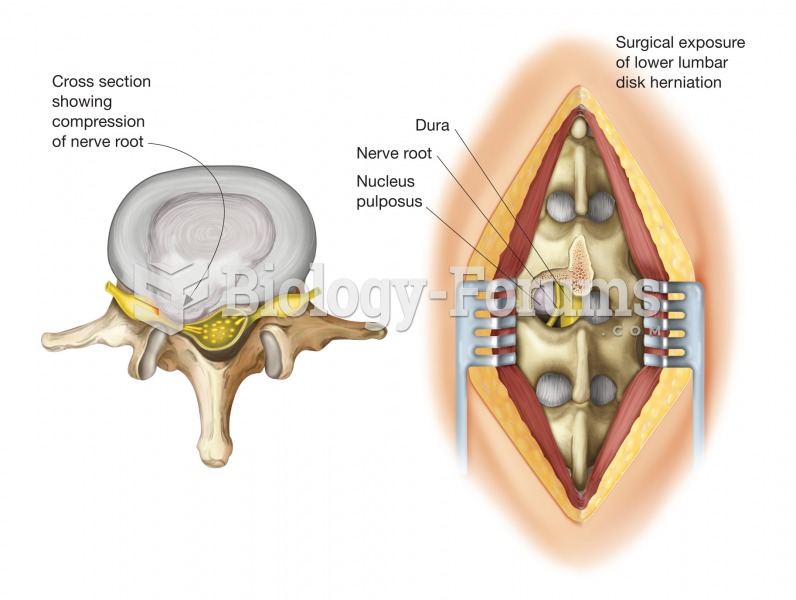
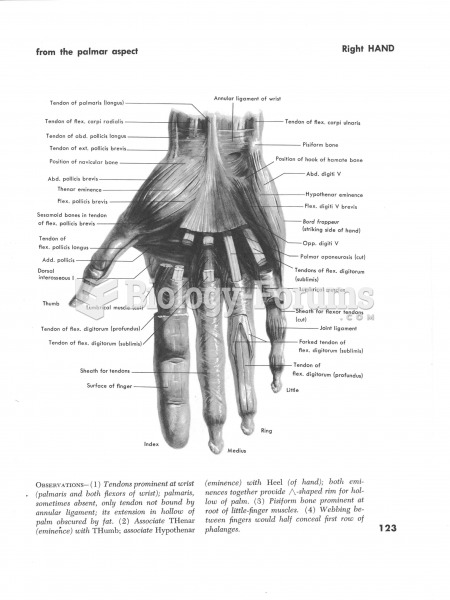
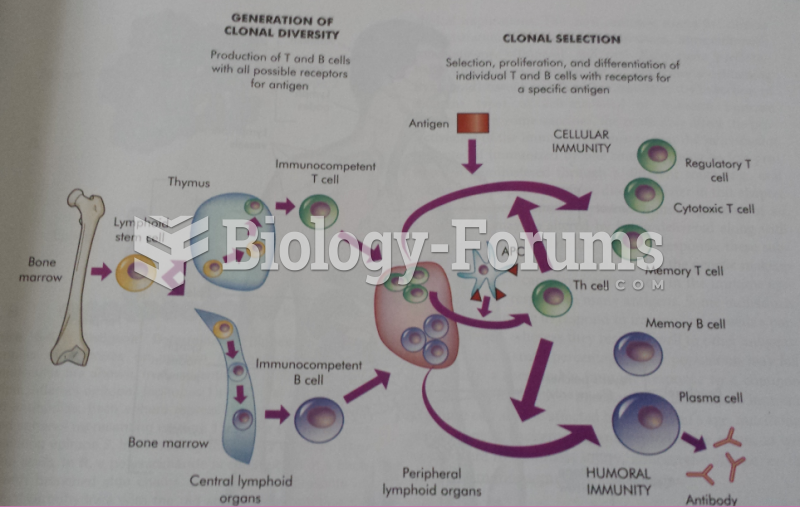
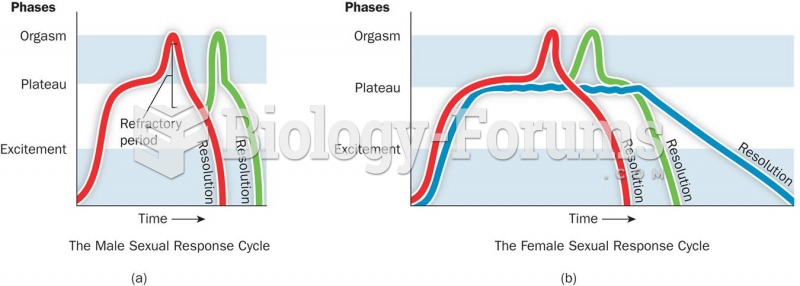
|
|
|
Adults are resistant to the bacterium that causes Botulism. These bacteria thrive in honey – therefore, honey should never be given to infants since their immune systems are not yet resistant.
The largest baby ever born weighed more than 23 pounds but died just 11 hours after his birth in 1879. The largest surviving baby was born in October 2009 in Sumatra, Indonesia, and weighed an astounding 19.2 pounds at birth.
In 1885, the Lloyd Manufacturing Company of Albany, New York, promoted and sold "Cocaine Toothache Drops" at 15 cents per bottle! In 1914, the Harrison Narcotic Act brought the sale and distribution of this drug under federal control.
About 3.2 billion people, nearly half the world population, are at risk for malaria. In 2015, there are about 214 million malaria cases and an estimated 438,000 malaria deaths.
Patients who cannot swallow may receive nutrition via a parenteral route—usually, a catheter is inserted through the chest into a large vein going into the heart.