|
|
|
Fatal fungal infections may be able to resist newer antifungal drugs. Globally, fungal infections are often fatal due to the lack of access to multiple antifungals, which may be required to be utilized in combination. Single antifungals may not be enough to stop a fungal infection from causing the death of a patient.
More than 34,000 trademarked medication names and more than 10,000 generic medication names are in use in the United States.
As many as 20% of Americans have been infected by the fungus known as Histoplasmosis. While most people are asymptomatic or only have slight symptoms, infection can progress to a rapid and potentially fatal superinfection.
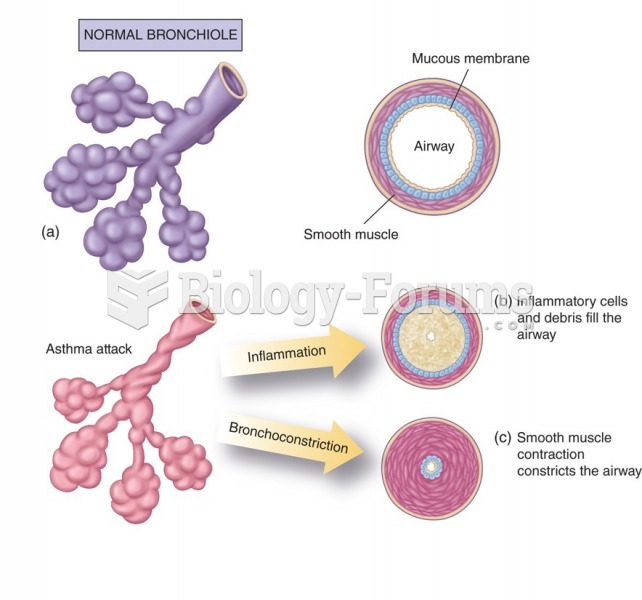
Asthma-like symptoms were first recorded about 3,500 years ago in Egypt. The first manuscript specifically written about asthma was in the year 1190, describing a condition characterized by sudden breathlessness. The treatments listed in this manuscript include chicken soup, herbs, and sexual abstinence.
Alcohol acts as a diuretic. Eight ounces of water is needed to metabolize just 1 ounce of alcohol.
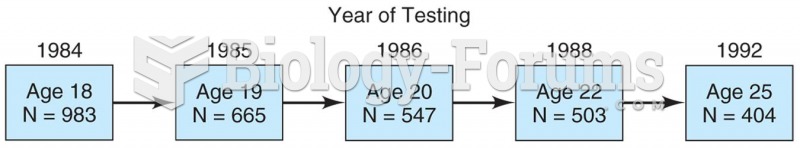 Model of a longitudinal study in which 983 students were surveyed in 1984 and then again in 1985, 19
Model of a longitudinal study in which 983 students were surveyed in 1984 and then again in 1985, 19
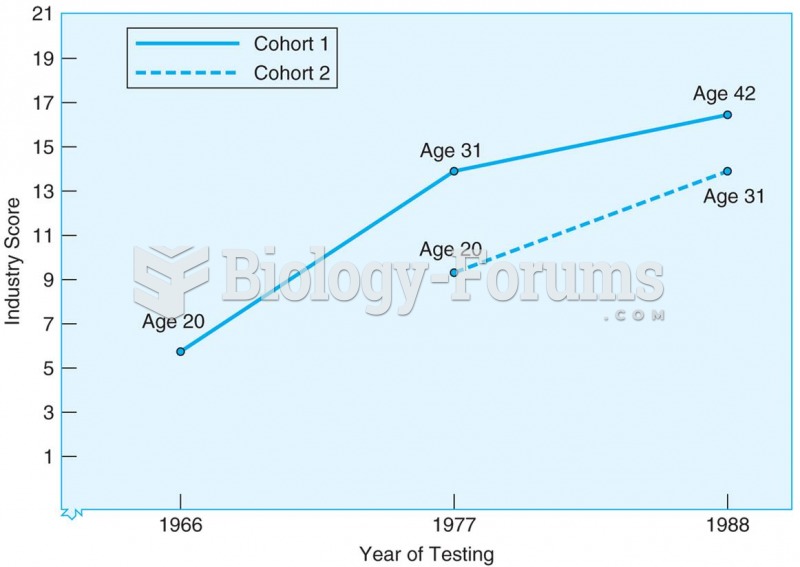 Results from sequential study of two cohorts tested at three ages and at three different points in t
Results from sequential study of two cohorts tested at three ages and at three different points in t