|
|
|
It is widely believed that giving a daily oral dose of aspirin to heart attack patients improves their chances of survival because the aspirin blocks the formation of new blood clots.
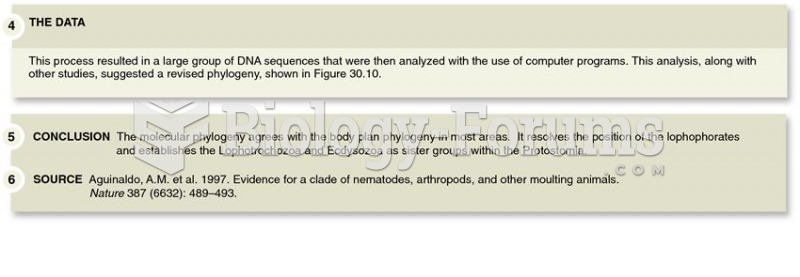
Your heart beats over 36 million times a year.
A serious new warning has been established for pregnant women against taking ACE inhibitors during pregnancy. In the study, the risk of major birth defects in children whose mothers took ACE inhibitors during the first trimester was nearly three times higher than in children whose mothers didn't take ACE inhibitors. Physicians can prescribe alternative medications for pregnant women who have symptoms of high blood pressure.
Most strokes are caused when blood clots move to a blood vessel in the brain and block blood flow to that area. Thrombolytic therapy can be used to dissolve the clot quickly. If given within 3 hours of the first stroke symptoms, this therapy can help limit stroke damage and disability.
Elderly adults are at greatest risk of stroke and myocardial infarction and have the most to gain from prophylaxis. Patients ages 60 to 80 years with blood pressures above 160/90 mm Hg should benefit from antihypertensive treatment.