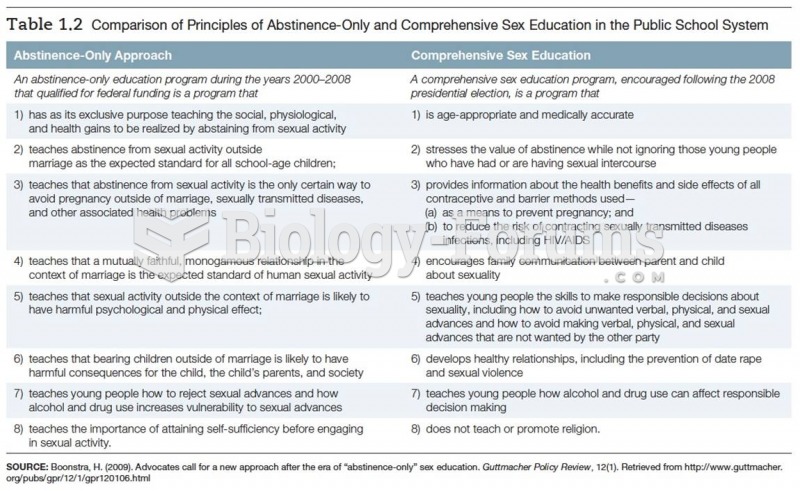
|
|
|
Long-term mental and physical effects from substance abuse include: paranoia, psychosis, immune deficiencies, and organ damage.
Never take aspirin without food because it is likely to irritate your stomach. Never give aspirin to children under age 12. Overdoses of aspirin have the potential to cause deafness.
Everyone has one nostril that is larger than the other.
Liver spots have nothing whatsoever to do with the liver. They are a type of freckles commonly seen in older adults who have been out in the sun without sufficient sunscreen.
A headache when you wake up in the morning is indicative of sinusitis. Other symptoms of sinusitis can include fever, weakness, tiredness, a cough that may be more severe at night, and a runny nose or nasal congestion.