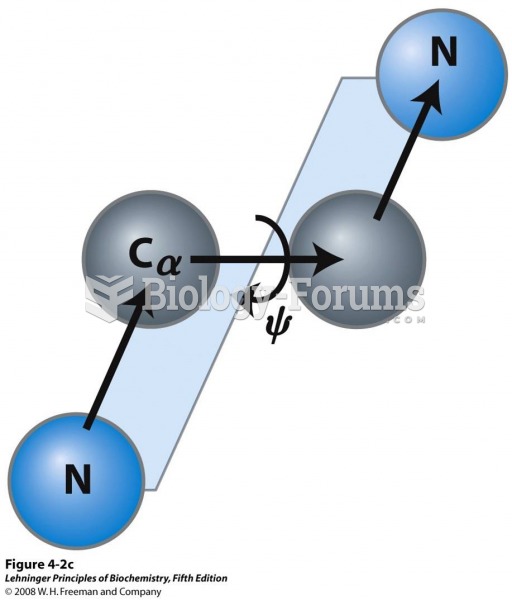
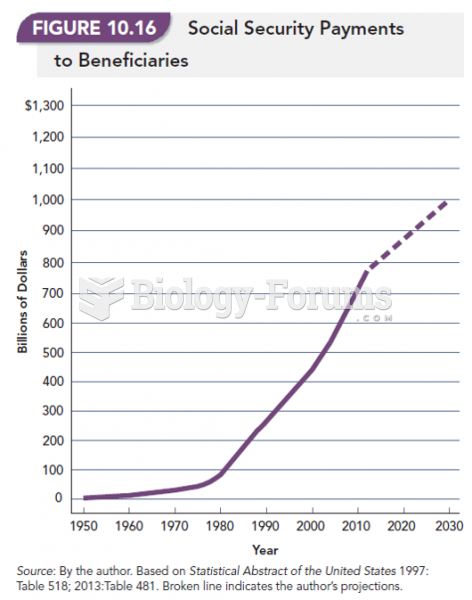
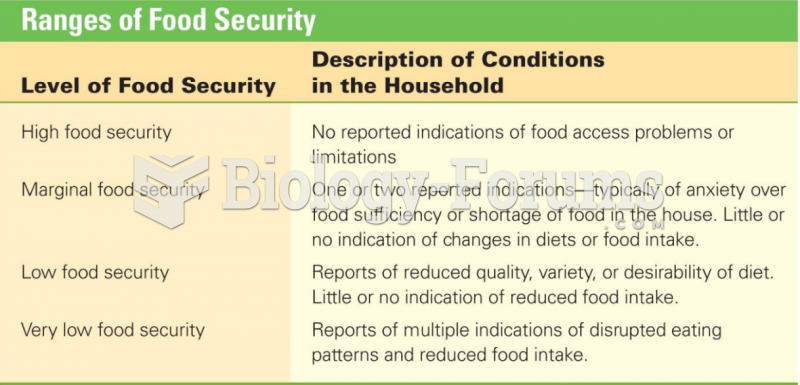
|
|
|
Approximately 500,000 babies are born each year in the United States to teenage mothers.
The eye muscles are the most active muscles in the whole body. The external muscles that move the eyes are the strongest muscles in the human body for the job they have to do. They are 100 times more powerful than they need to be.
Over time, chronic hepatitis B virus and hepatitis C virus infections can progress to advanced liver disease, liver failure, and hepatocellular carcinoma. Unlike other forms, more than 80% of hepatitis C infections become chronic and lead to liver disease. When combined with hepatitis B, hepatitis C now accounts for 75% percent of all cases of liver disease around the world. Liver failure caused by hepatitis C is now leading cause of liver transplants in the United States.
Certain chemicals, after ingestion, can be converted by the body into cyanide. Most of these chemicals have been removed from the market, but some old nail polish remover, solvents, and plastics manufacturing solutions can contain these substances.
All adults should have their cholesterol levels checked once every 5 years. During 2009–2010, 69.4% of Americans age 20 and older reported having their cholesterol checked within the last five years.