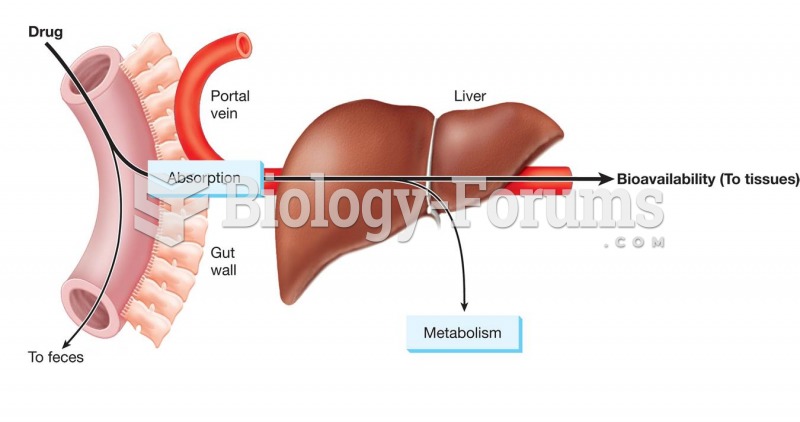
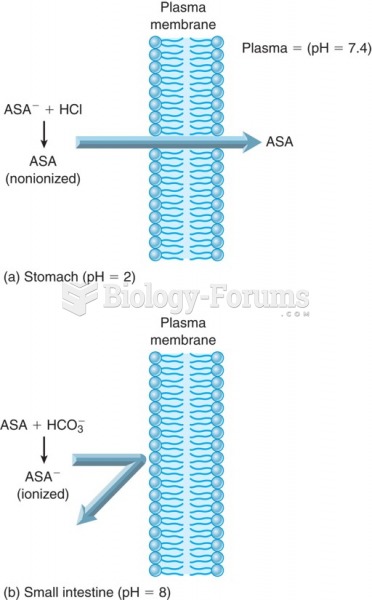
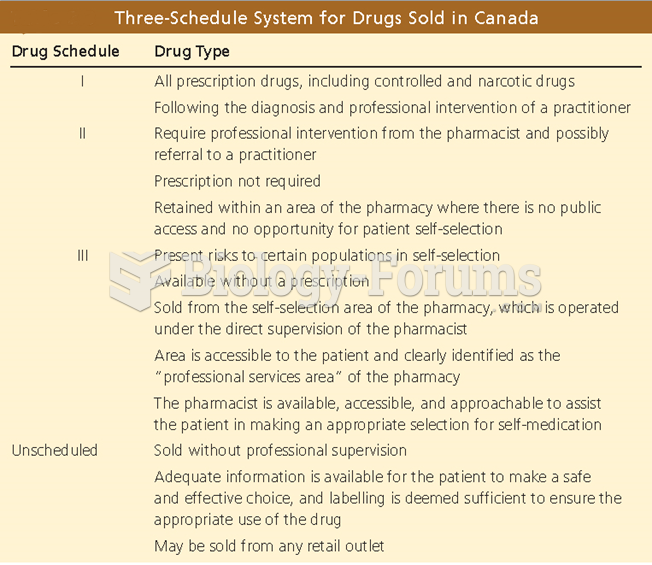
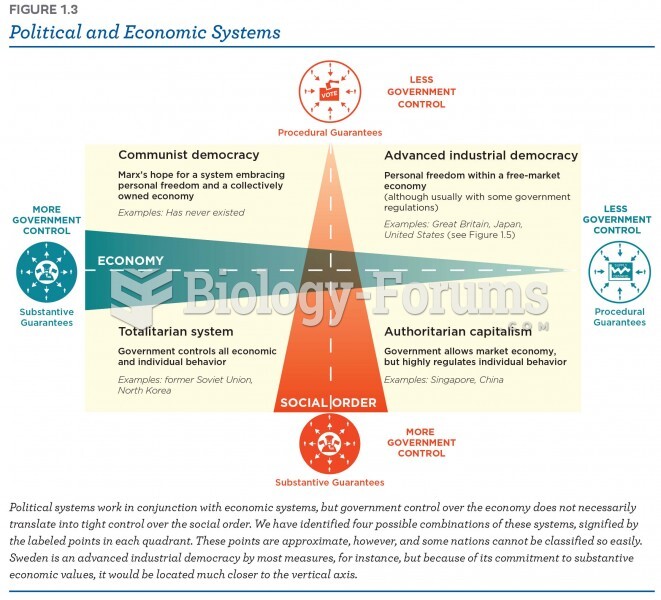
|
|
|
Adolescents often feel clumsy during puberty because during this time of development, their hands and feet grow faster than their arms and legs do. The body is therefore out of proportion. One out of five adolescents actually experiences growing pains during this period.
Alzheimer's disease affects only about 10% of people older than 65 years of age. Most forms of decreased mental function and dementia are caused by disuse (letting the mind get lazy).
Essential fatty acids have been shown to be effective against ulcers, asthma, dental cavities, and skin disorders such as acne.
Amphetamine poisoning can cause intravascular coagulation, circulatory collapse, rhabdomyolysis, ischemic colitis, acute psychosis, hyperthermia, respiratory distress syndrome, and pericarditis.
In women, pharmacodynamic differences include increased sensitivity to (and increased effectiveness of) beta-blockers, opioids, selective serotonin reuptake inhibitors, and typical antipsychotics.