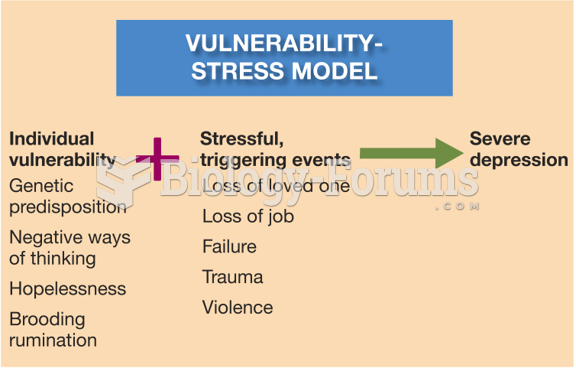
|
|
|
Automated pill dispensing systems have alarms to alert patients when the correct dosing time has arrived. Most systems work with many varieties of medications, so patients who are taking a variety of drugs can still be in control of their dose regimen.
Sperm cells are so tiny that 400 to 500 million (400,000,000–500,000,000) of them fit onto 1 tsp.
More than nineteen million Americans carry the factor V gene that causes blood clots, pulmonary embolism, and heart disease.
A good example of polar molecules can be understood when trying to make a cake. If water and oil are required, they will not mix together. If you put them into a measuring cup, the oil will rise to the top while the water remains on the bottom.
Approximately one in three babies in the United States is now delivered by cesarean section. The number of cesarean sections in the United States has risen 46% since 1996.
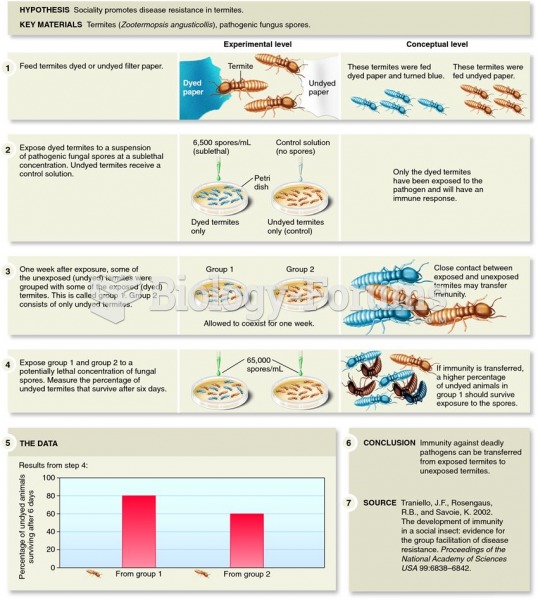 Traniello and his colleagues demonstrated that social insects may develop “social imm
Traniello and his colleagues demonstrated that social insects may develop “social imm
 The recent mass upheavals in Tunisia, Egypt, Libya, Yemen, and Syria gave political scientists a cha
The recent mass upheavals in Tunisia, Egypt, Libya, Yemen, and Syria gave political scientists a cha
 Differences in how we display gender often lie below our awareness. How males and females use social ...
Differences in how we display gender often lie below our awareness. How males and females use social ...