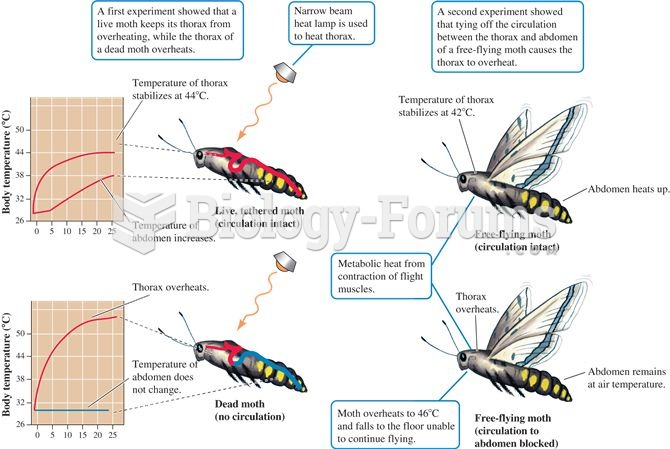
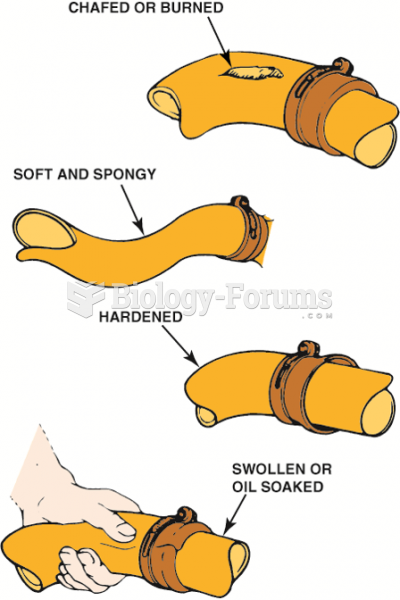
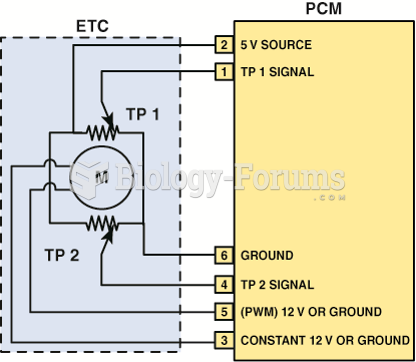
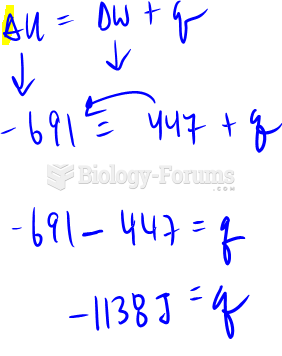
|
|
|
Although the Roman numeral for the number 4 has always been taught to have been "IV," according to historians, the ancient Romans probably used "IIII" most of the time. This is partially backed up by the fact that early grandfather clocks displayed IIII for the number 4 instead of IV. Early clockmakers apparently thought that the IIII balanced out the VIII (used for the number 8) on the clock face and that it just looked better.
IgA antibodies protect body surfaces exposed to outside foreign substances. IgG antibodies are found in all body fluids. IgM antibodies are the first type of antibody made in response to an infection. IgE antibody levels are often high in people with allergies. IgD antibodies are found in tissues lining the abdomen and chest.
A good example of polar molecules can be understood when trying to make a cake. If water and oil are required, they will not mix together. If you put them into a measuring cup, the oil will rise to the top while the water remains on the bottom.
The first successful kidney transplant was performed in 1954 and occurred in Boston. A kidney from an identical twin was transplanted into his dying brother's body and was not rejected because it did not appear foreign to his body.
It is difficult to obtain enough calcium without consuming milk or other dairy foods.