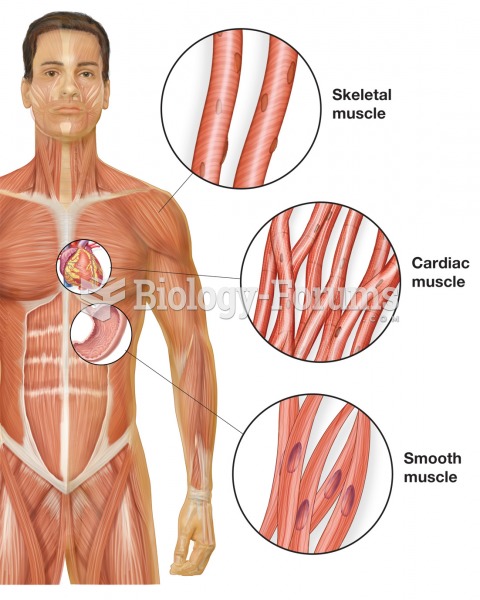
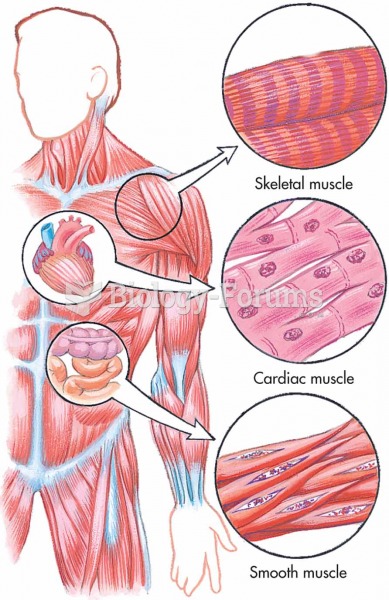
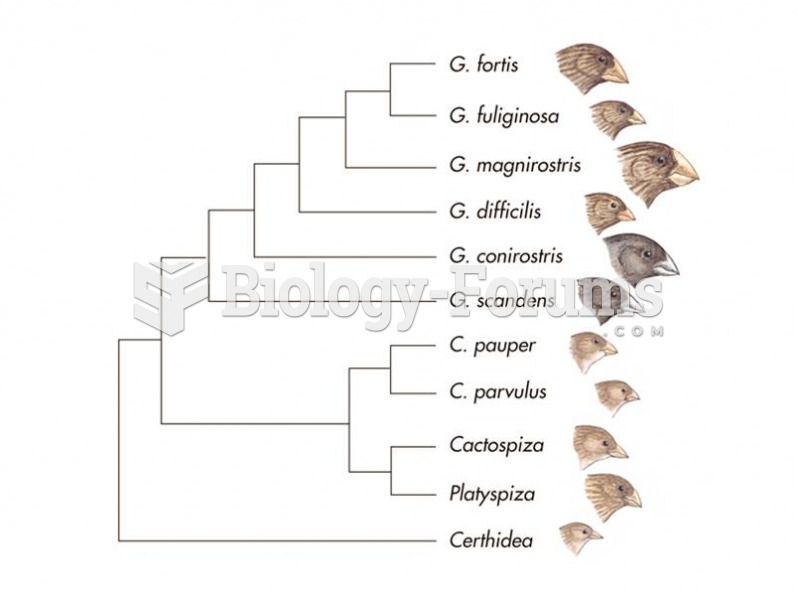
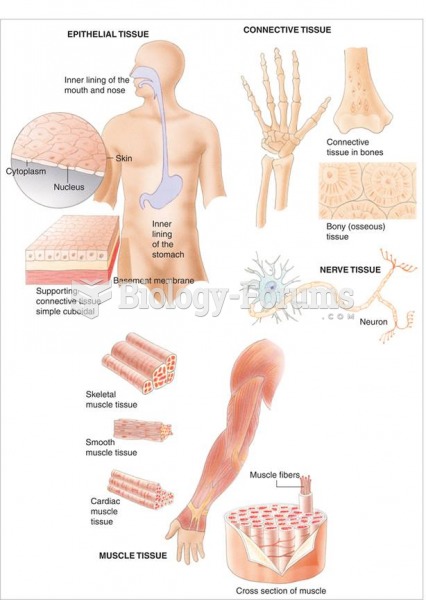
|
|
|
Your chance of developing a kidney stone is 1 in 10. In recent years, approximately 3.7 million people in the United States were diagnosed with a kidney disease.
Vaccines cause herd immunity. If the majority of people in a community have been vaccinated against a disease, an unvaccinated person is less likely to get the disease since others are less likely to become sick from it and spread the disease.
There are 60,000 miles of blood vessels in every adult human.
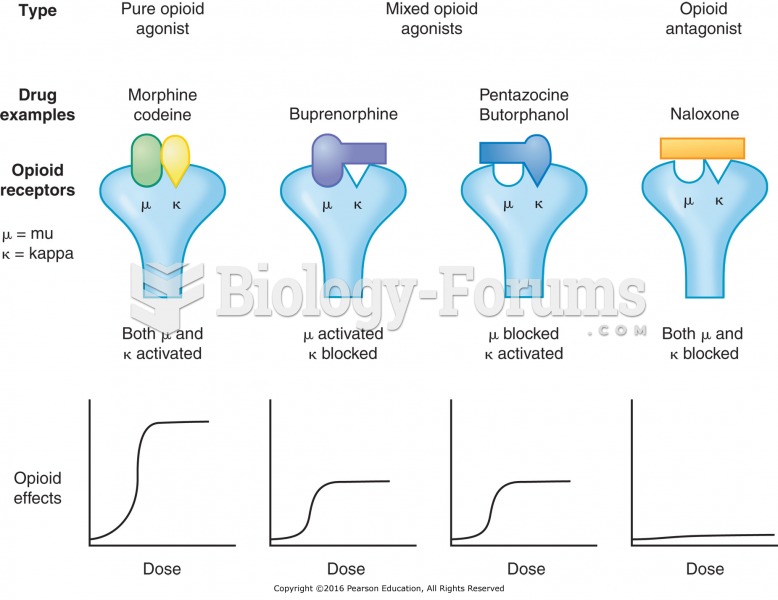
There are major differences in the metabolism of morphine and the illegal drug heroin. Morphine mostly produces its CNS effects through m-receptors, and at k- and d-receptors. Heroin has a slight affinity for opiate receptors. Most of its actions are due to metabolism to active metabolites (6-acetylmorphine, morphine, and morphine-6-glucuronide).
About one in five American adults and teenagers have had a genital herpes infection—and most of them don't know it. People with genital herpes have at least twice the risk of becoming infected with HIV if exposed to it than those people who do not have genital herpes.