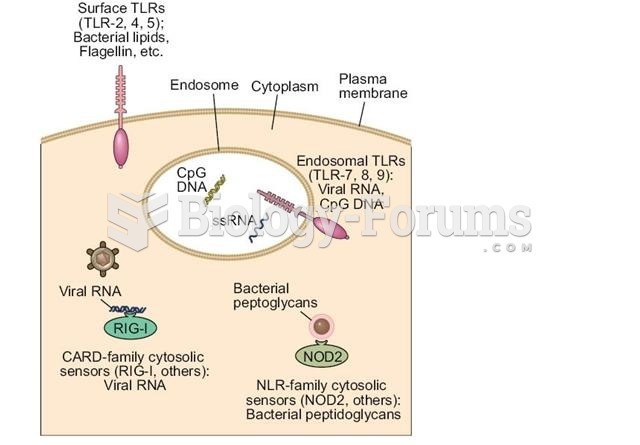
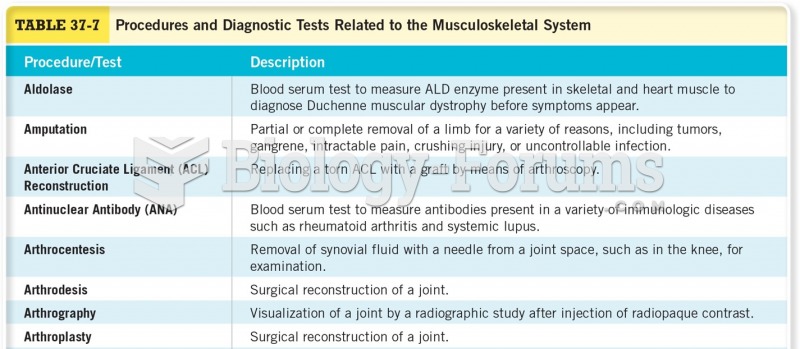
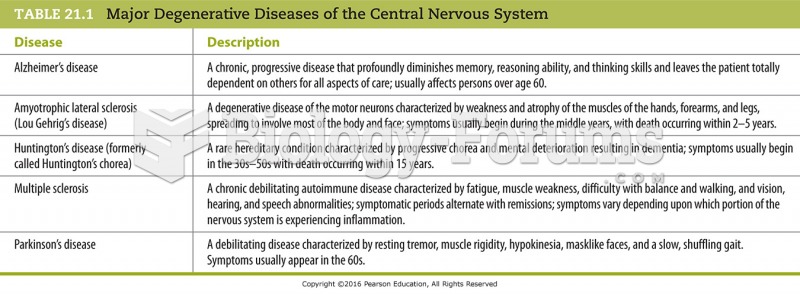
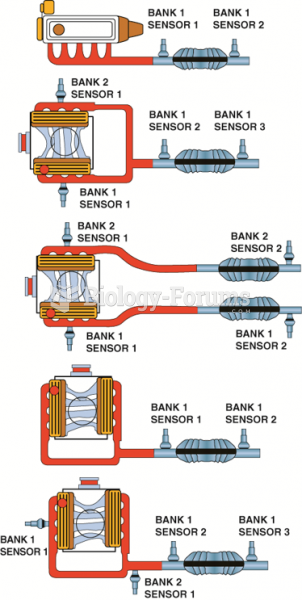
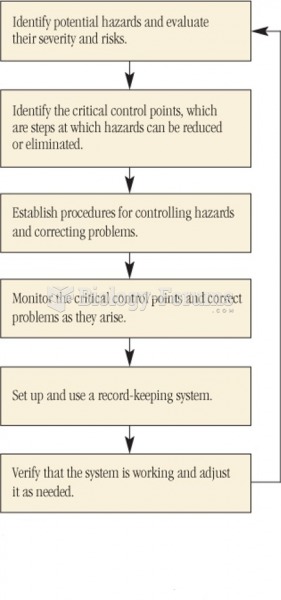
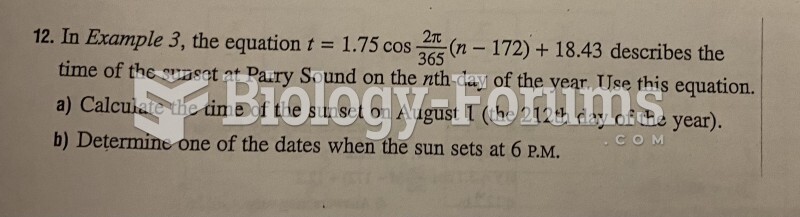This topic contains a solution. Click here to go to the answer
|
|
|
Did you know?
Sperm cells are so tiny that 400 to 500 million (400,000,000–500,000,000) of them fit onto 1 tsp.
Did you know?
There are approximately 3 million unintended pregnancies in the United States each year.
Did you know?
Astigmatism is the most common vision problem. It may accompany nearsightedness or farsightedness. It is usually caused by an irregularly shaped cornea, but sometimes it is the result of an irregularly shaped lens. Either type can be corrected by eyeglasses, contact lenses, or refractive surgery.
Did you know?
Essential fatty acids have been shown to be effective against ulcers, asthma, dental cavities, and skin disorders such as acne.
Did you know?
About 600,000 particles of skin are shed every hour by each human. If you live to age 70 years, you have shed 105 pounds of dead skin.