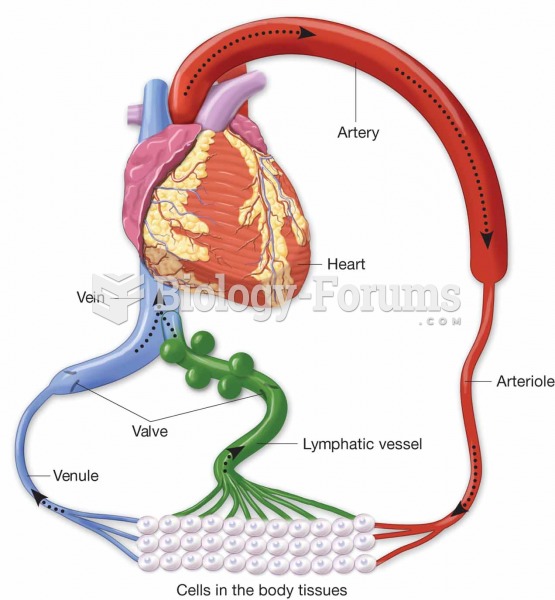
|
|
|
In most cases, kidneys can recover from almost complete loss of function, such as in acute kidney (renal) failure.
Thyroid conditions cause a higher risk of fibromyalgia and chronic fatigue syndrome.
On average, someone in the United States has a stroke about every 40 seconds. This is about 795,000 people per year.
In the ancient and medieval periods, dysentery killed about ? of all babies before they reach 12 months of age. The disease was transferred through contaminated drinking water, because there was no way to adequately dispose of sewage, which contaminated the water.
Alzheimer's disease affects only about 10% of people older than 65 years of age. Most forms of decreased mental function and dementia are caused by disuse (letting the mind get lazy).