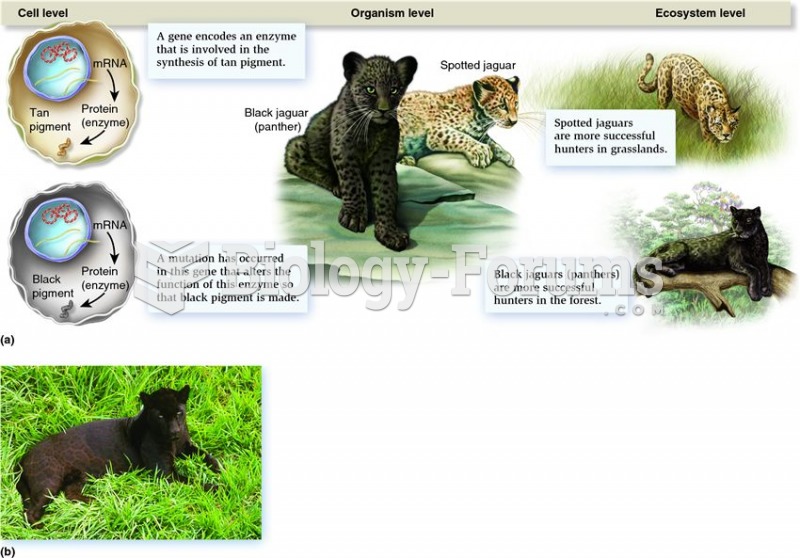
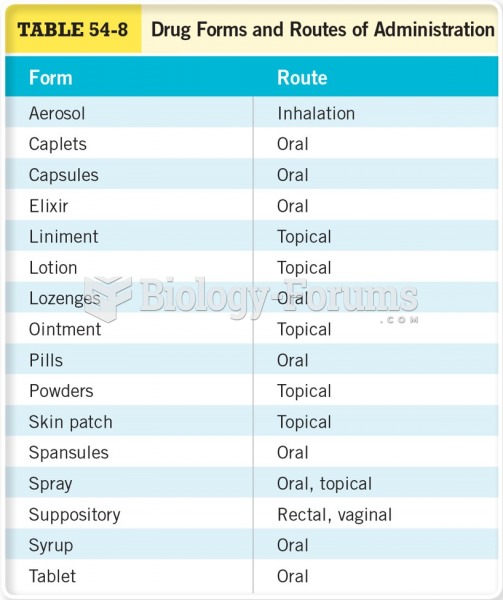
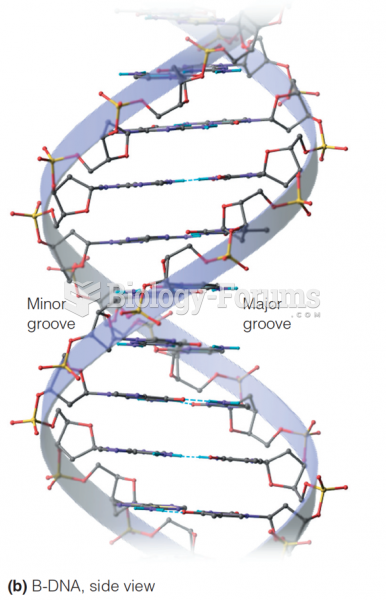
|
|
|
Nitroglycerin is used to alleviate various heart-related conditions, and it is also the chief component of dynamite (but mixed in a solid clay base to stabilize it).
Pink eye is a term that refers to conjunctivitis, which is inflammation of the thin, clear membrane (conjunctiva) over the white part of the eye (sclera). It may be triggered by a virus, bacteria, or foreign body in the eye. Antibiotic eye drops alleviate bacterial conjunctivitis, and antihistamine allergy pills or eye drops help control allergic conjunctivitis symptoms.
For pediatric patients, intravenous fluids are the most commonly cited products involved in medication errors that are reported to the USP.
Many supplement containers do not even contain what their labels say. There are many documented reports of products containing much less, or more, that what is listed on their labels. They may also contain undisclosed prescription drugs and even contaminants.
After a vasectomy, it takes about 12 ejaculations to clear out sperm that were already beyond the blocked area.