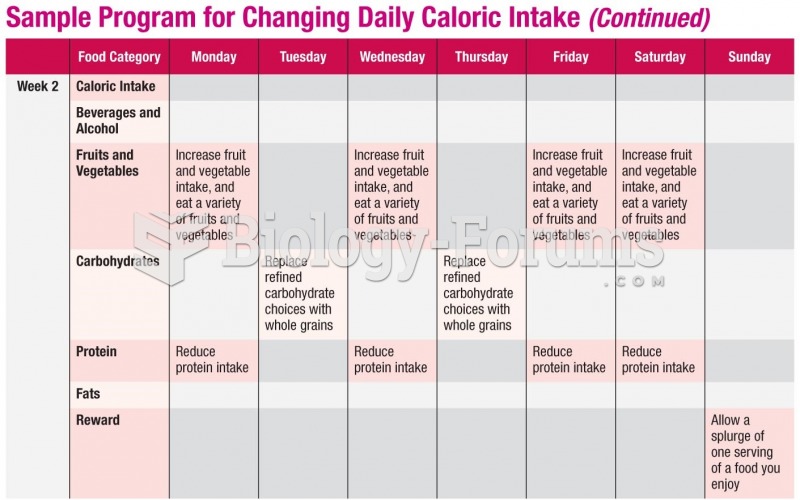
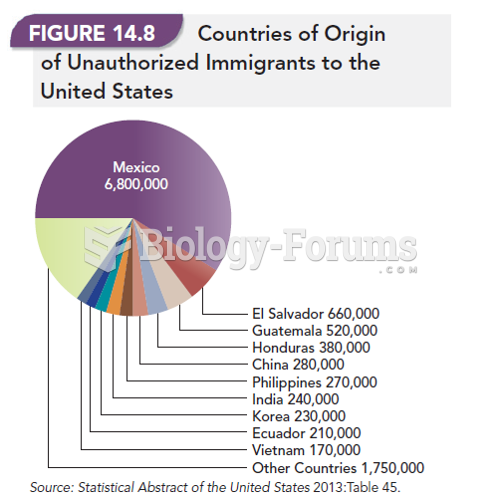
|
|
|
Today, nearly 8 out of 10 pregnant women living with HIV (about 1.1 million), receive antiretrovirals.
Adult head lice are gray, about ? inch long, and often have a tiny dot on their backs. A female can lay between 50 and 150 eggs within the several weeks that she is alive. They feed on human blood.
A strange skin disease referred to as Morgellons has occurred in the southern United States and in California. Symptoms include slowly healing sores, joint pain, persistent fatigue, and a sensation of things crawling through the skin. Another symptom is strange-looking, threadlike extrusions coming out of the skin.
Acetaminophen (Tylenol) in overdose can seriously damage the liver. It should never be taken by people who use alcohol heavily; it can result in severe liver damage and even a condition requiring a liver transplant.
Opium has influenced much of the world's most popular literature. The following authors were all opium users, of varying degrees: Lewis Carroll, Charles, Dickens, Arthur Conan Doyle, and Oscar Wilde.