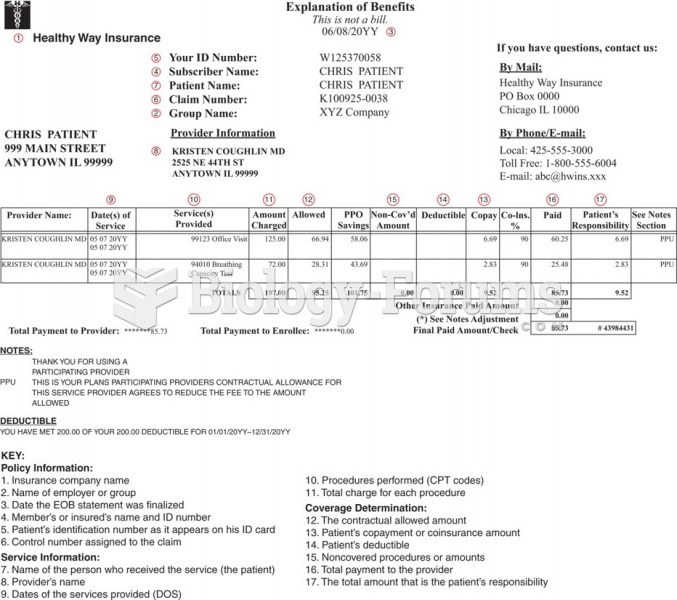
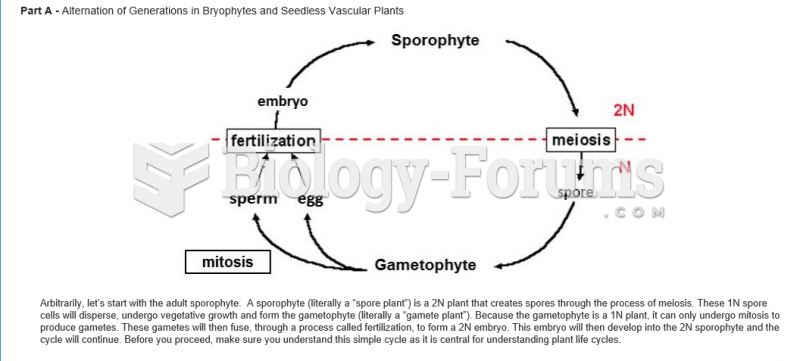
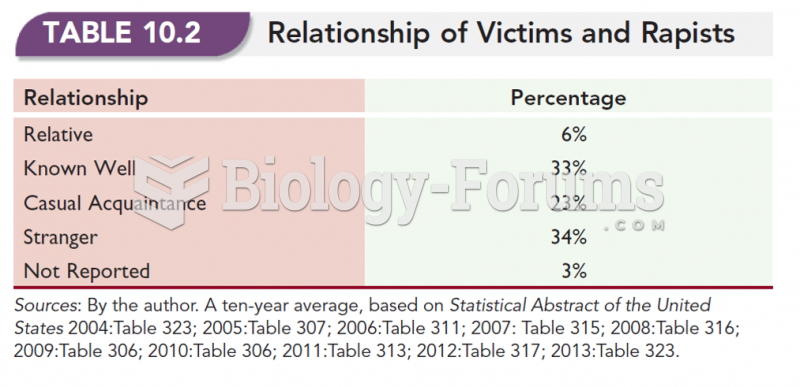
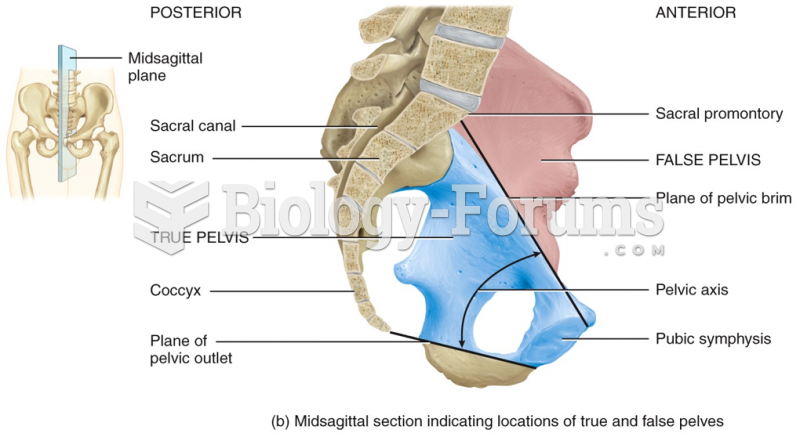
|
|
|
Common abbreviations that cause medication errors include U (unit), mg (milligram), QD (every day), SC (subcutaneous), TIW (three times per week), D/C (discharge or discontinue), HS (at bedtime or "hours of sleep"), cc (cubic centimeters), and AU (each ear).
Bacteria have been found alive in a lake buried one half mile under ice in Antarctica.
Most fungi that pathogenically affect humans live in soil. If a person is not healthy, has an open wound, or is immunocompromised, a fungal infection can be very aggressive.
Asthma-like symptoms were first recorded about 3,500 years ago in Egypt. The first manuscript specifically written about asthma was in the year 1190, describing a condition characterized by sudden breathlessness. The treatments listed in this manuscript include chicken soup, herbs, and sexual abstinence.
Women are 50% to 75% more likely than men to experience an adverse drug reaction.