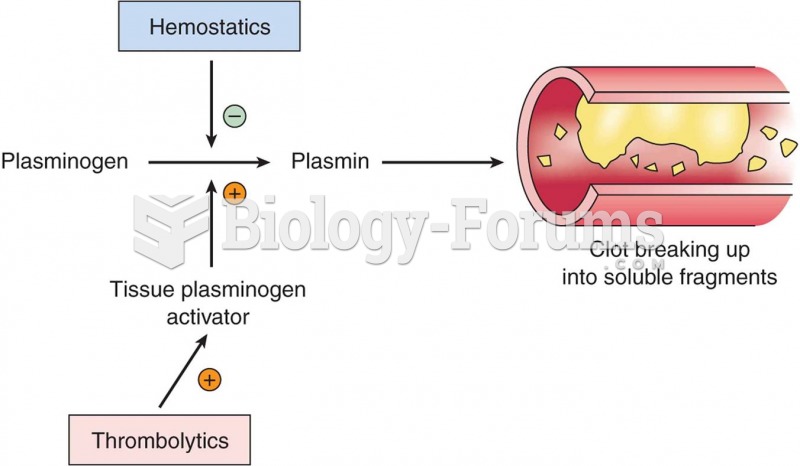
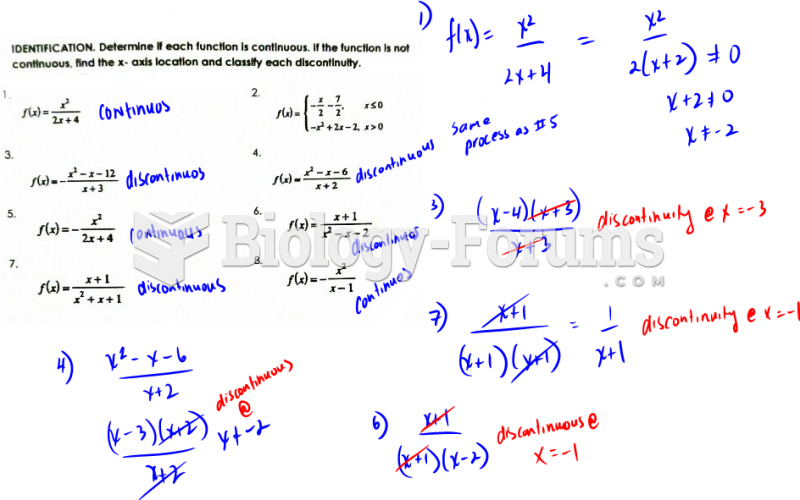
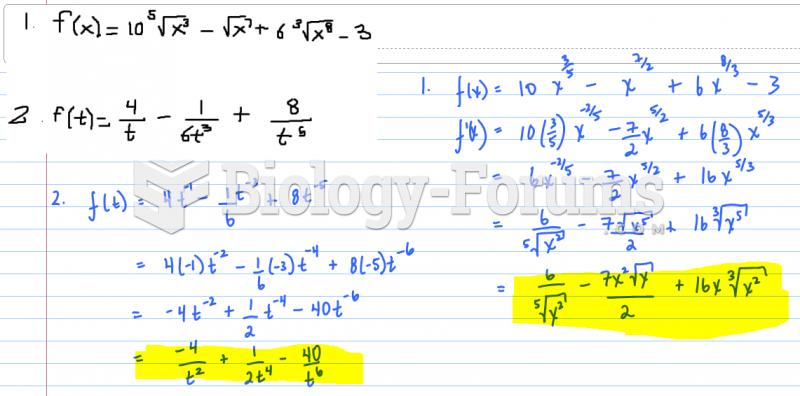
This topic contains a solution. Click here to go to the answer
|
|
|
Did you know?
Thyroid conditions cause a higher risk of fibromyalgia and chronic fatigue syndrome.
Did you know?
Human stomach acid is strong enough to dissolve small pieces of metal such as razor blades or staples.
Did you know?
The term pharmacology is derived from the Greek words pharmakon("claim, medicine, poison, or remedy") and logos ("study").
Did you know?
Vaccines prevent between 2.5 and 4 million deaths every year.
Did you know?
Although puberty usually occurs in the early teenage years, the world's youngest parents were two Chinese children who had their first baby when they were 8 and 9 years of age.