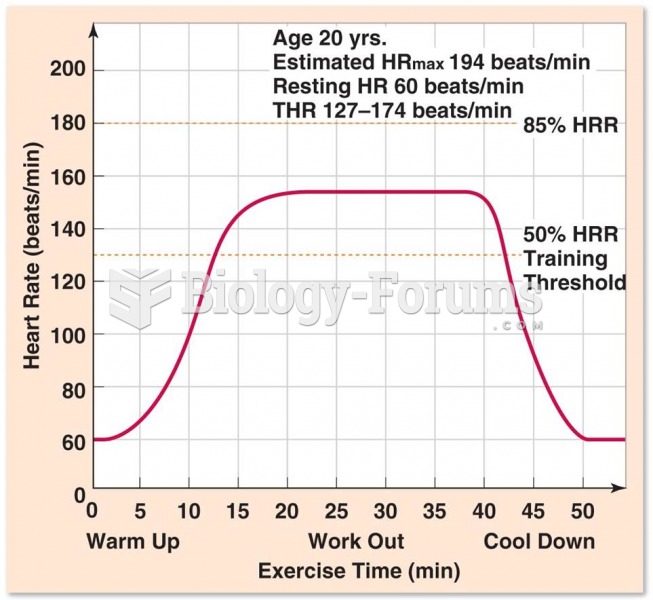
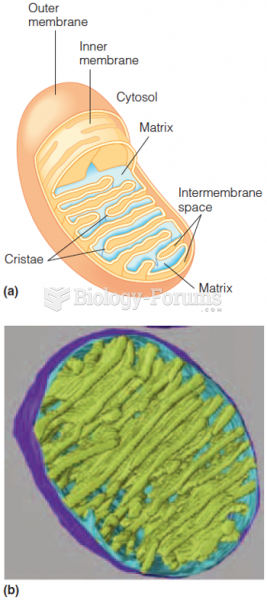
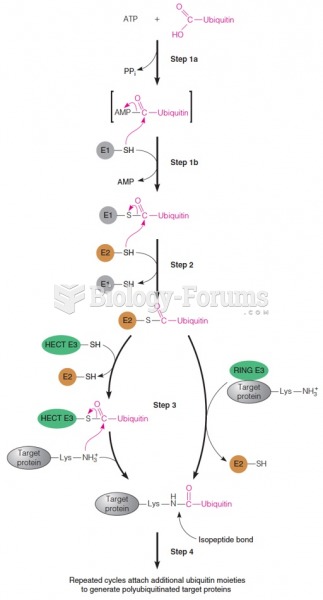
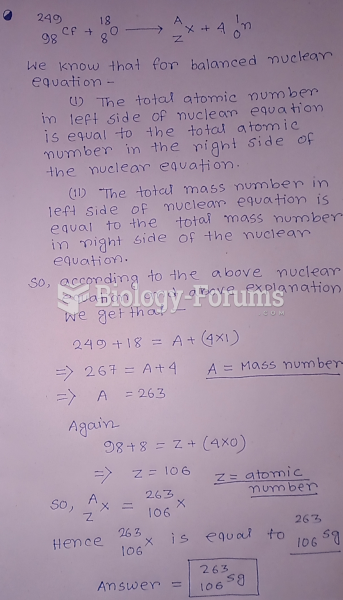
|
|
|
When taking monoamine oxidase inhibitors, people should avoid a variety of foods, which include alcoholic beverages, bean curd, broad (fava) bean pods, cheese, fish, ginseng, protein extracts, meat, sauerkraut, shrimp paste, soups, and yeast.
Acetaminophen (Tylenol) in overdose can seriously damage the liver. It should never be taken by people who use alcohol heavily; it can result in severe liver damage and even a condition requiring a liver transplant.
The calories found in one piece of cherry cheesecake could light a 60-watt light bulb for 1.5 hours.
Hippocrates noted that blood separates into four differently colored liquids when removed from the body and examined: a pure red liquid mixed with white liquid material with a yellow-colored froth at the top and a black substance that settles underneath; he named these the four humors (for blood, phlegm, yellow bile, and black bile).