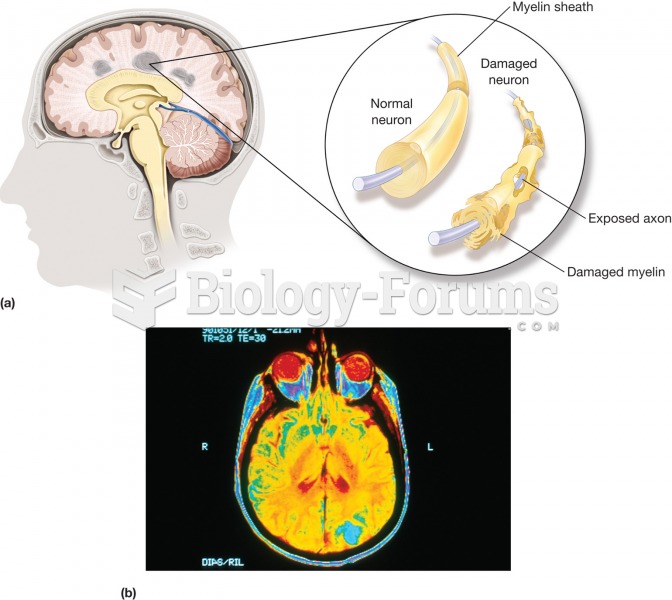
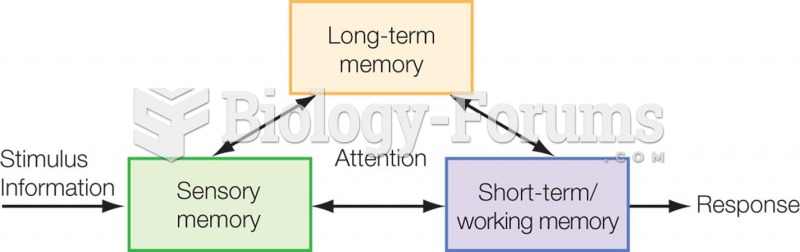
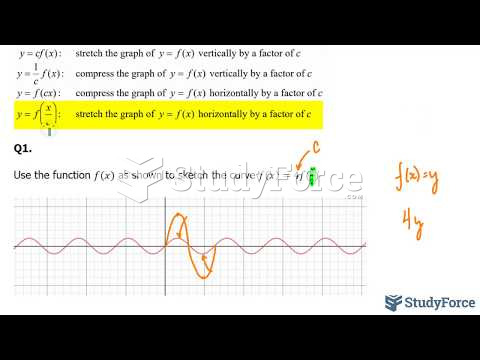
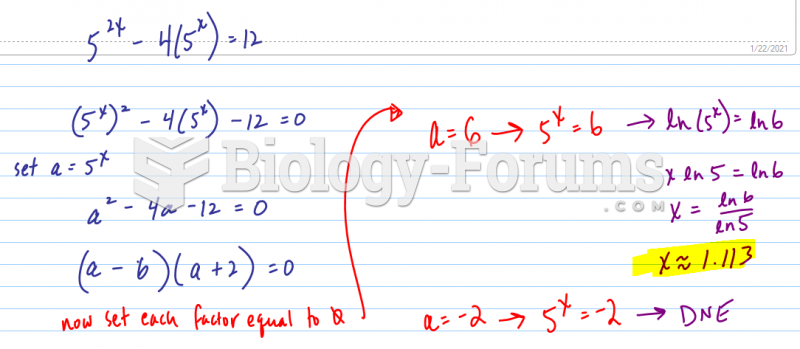
|
|
|
Complications of influenza include: bacterial pneumonia, ear and sinus infections, dehydration, and worsening of chronic conditions such as asthma, congestive heart failure, or diabetes.
Chronic marijuana use can damage the white blood cells and reduce the immune system's ability to respond to disease by as much as 40%. Without a strong immune system, the body is vulnerable to all kinds of degenerative and infectious diseases.
Automated pill dispensing systems have alarms to alert patients when the correct dosing time has arrived. Most systems work with many varieties of medications, so patients who are taking a variety of drugs can still be in control of their dose regimen.
Interferon was scarce and expensive until 1980, when the interferon gene was inserted into bacteria using recombinant DNA technology, allowing for mass cultivation and purification from bacterial cultures.
Every 10 seconds, a person in the United States goes to the emergency room complaining of head pain. About 1.2 million visits are for acute migraine attacks.