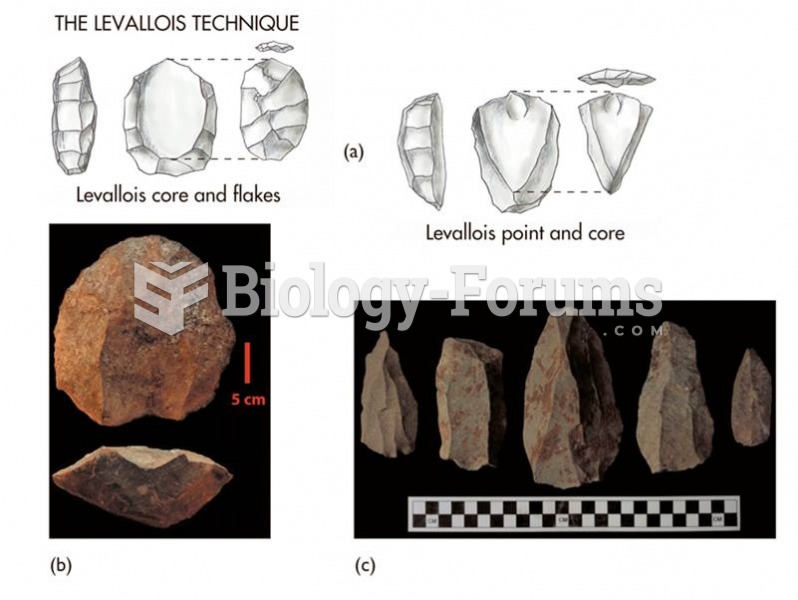
|
|
|
In 2012, nearly 24 milliion Americans, aged 12 and older, had abused an illicit drug, according to the National Institute on Drug Abuse (NIDA).
Opium has influenced much of the world's most popular literature. The following authors were all opium users, of varying degrees: Lewis Carroll, Charles, Dickens, Arthur Conan Doyle, and Oscar Wilde.
All patients with hyperparathyroidism will develop osteoporosis. The parathyroid glands maintain blood calcium within the normal range. All patients with this disease will continue to lose calcium from their bones every day, and there is no way to prevent the development of osteoporosis as a result.
About 100 new prescription or over-the-counter drugs come into the U.S. market every year.
Adult head lice are gray, about ? inch long, and often have a tiny dot on their backs. A female can lay between 50 and 150 eggs within the several weeks that she is alive. They feed on human blood.
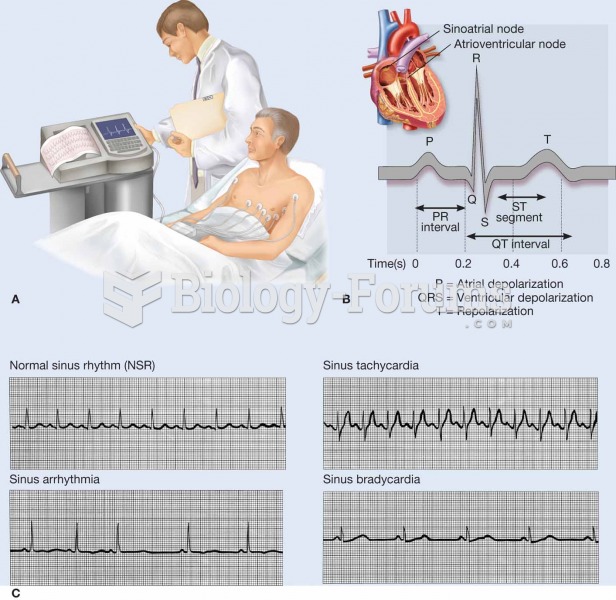 An electrocardiogram (ECG, EKG) is a commonly used procedure in which the electrical events associat
An electrocardiogram (ECG, EKG) is a commonly used procedure in which the electrical events associat
 Charles Darwin may be dead and gone but a recent write-in campaign has pitted him against Republican
Charles Darwin may be dead and gone but a recent write-in campaign has pitted him against Republican
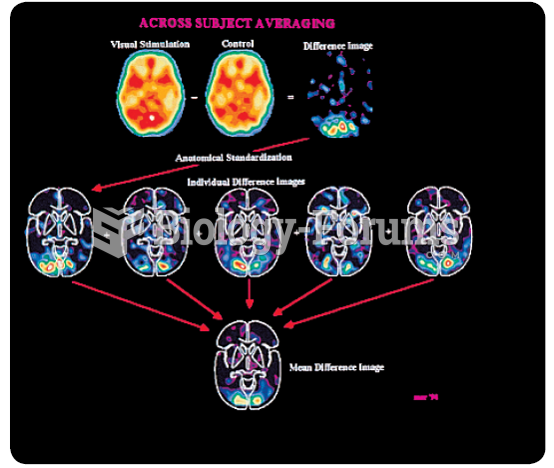 The paired-image subtraction technique, which is commonly employed in cognitive neuroscience. Here ...
The paired-image subtraction technique, which is commonly employed in cognitive neuroscience. Here ...