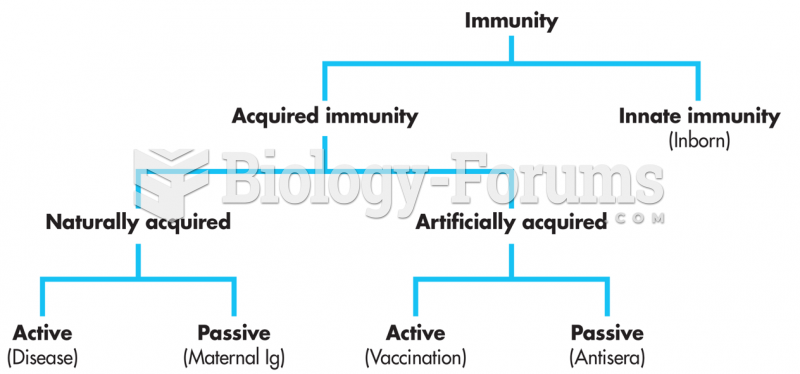
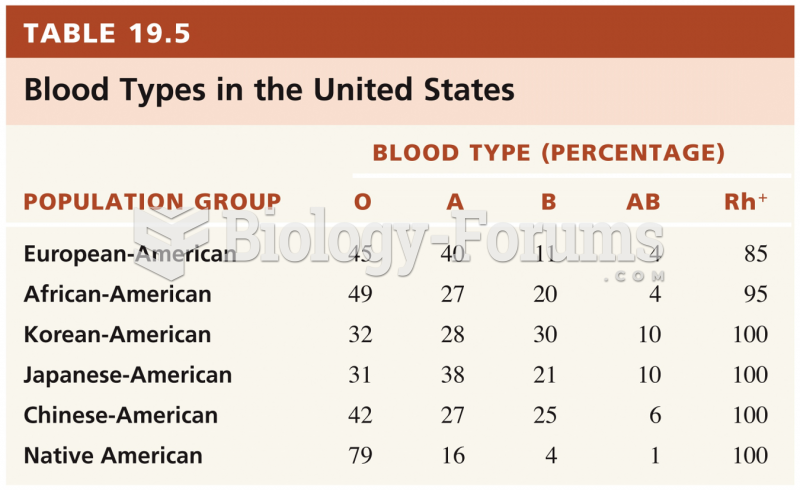
|
|
|
Your skin wrinkles if you stay in the bathtub a long time because the outermost layer of skin (which consists of dead keratin) swells when it absorbs water. It is tightly attached to the skin below it, so it compensates for the increased area by wrinkling. This happens to the hands and feet because they have the thickest layer of dead keratin cells.
Long-term mental and physical effects from substance abuse include: paranoia, psychosis, immune deficiencies, and organ damage.
About 60% of newborn infants in the United States are jaundiced; that is, they look yellow. Kernicterus is a form of brain damage caused by excessive jaundice. When babies begin to be affected by excessive jaundice and begin to have brain damage, they become excessively lethargic.
ACTH levels are normally highest in the early morning (between 6 and 8 A.M.) and lowest in the evening (between 6 and 11 P.M.). Therefore, a doctor who suspects abnormal levels looks for low ACTH in the morning and high ACTH in the evening.
In 1835 it was discovered that a disease of silkworms known as muscardine could be transferred from one silkworm to another, and was caused by a fungus.