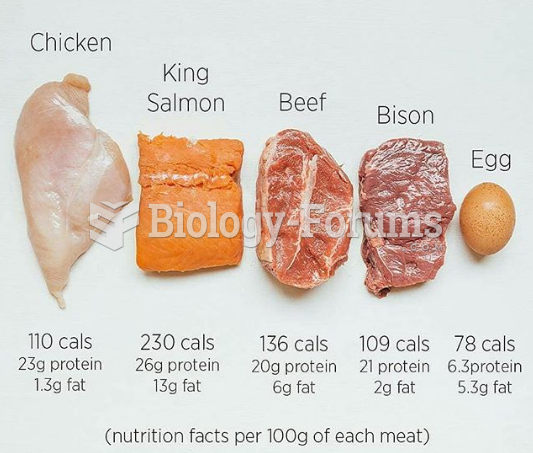
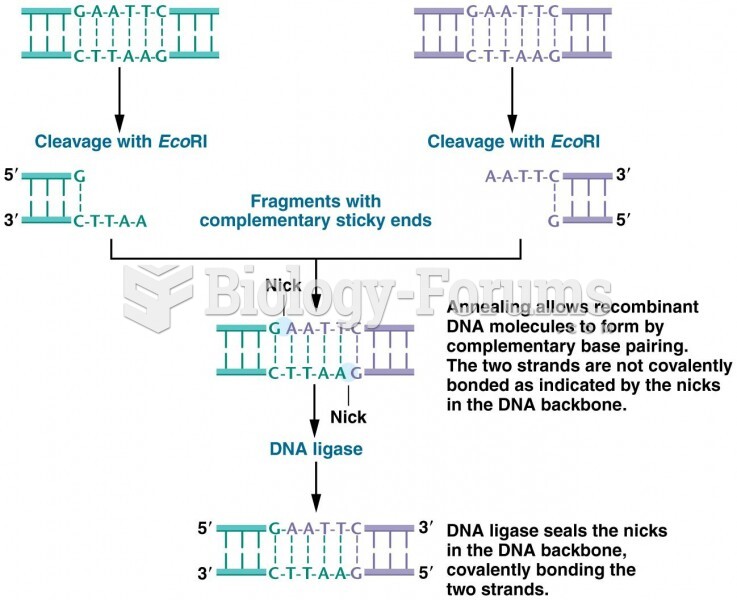
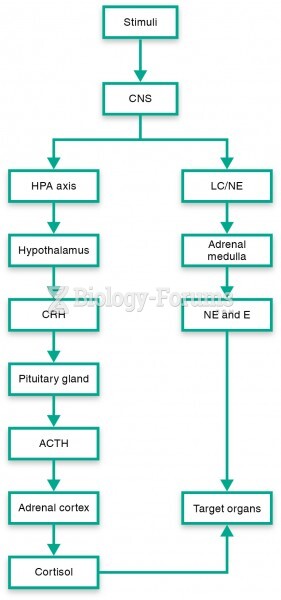
|
|
|
Alcohol acts as a diuretic. Eight ounces of water is needed to metabolize just 1 ounce of alcohol.
Atropine was named after the Greek goddess Atropos, the oldest and ugliest of the three sisters known as the Fates, who controlled the destiny of men.
It is believed that humans initially contracted crabs from gorillas about 3 million years ago from either sleeping in gorilla nests or eating the apes.
Amphetamine poisoning can cause intravascular coagulation, circulatory collapse, rhabdomyolysis, ischemic colitis, acute psychosis, hyperthermia, respiratory distress syndrome, and pericarditis.
When blood is deoxygenated and flowing back to the heart through the veins, it is dark reddish-blue in color. Blood in the arteries that is oxygenated and flowing out to the body is bright red. Whereas arterial blood comes out in spurts, venous blood flows.