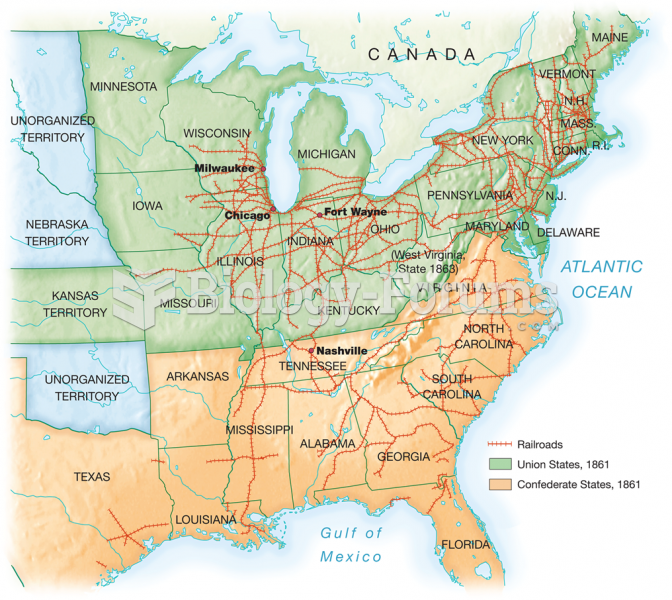
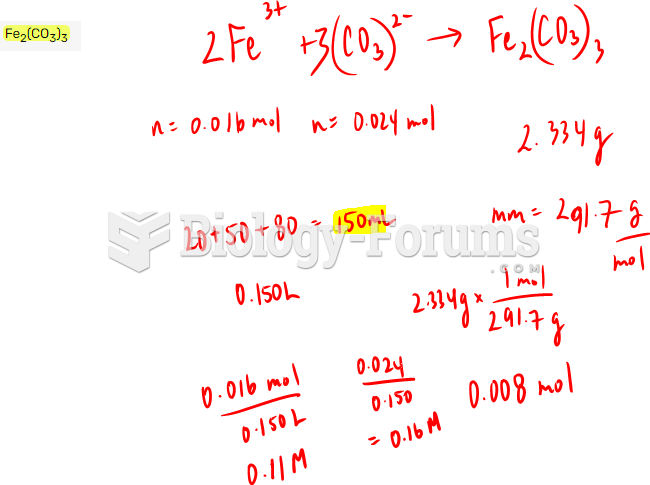
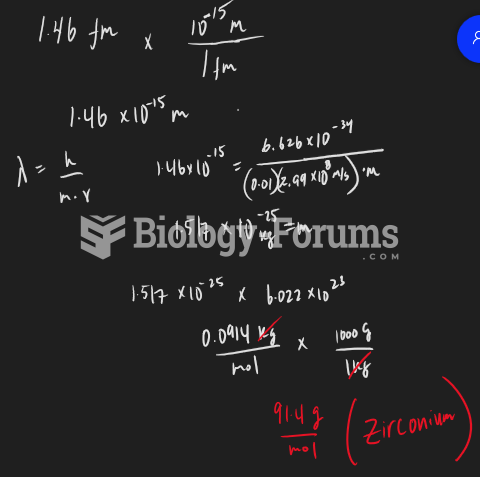
|
|
|
Essential fatty acids have been shown to be effective against ulcers, asthma, dental cavities, and skin disorders such as acne.
Drying your hands with a paper towel will reduce the bacterial count on your hands by 45–60%.
Warfarin was developed as a consequence of the study of a strange bleeding disorder that suddenly occurred in cattle on the northern prairies of the United States in the early 1900s.
The U.S. Preventive Services Task Force recommends that all women age 65 years of age or older should be screened with bone densitometry.
Blastomycosis is often misdiagnosed, resulting in tragic outcomes. It is caused by a fungus living in moist soil, in wooded areas of the United States and Canada. If inhaled, the fungus can cause mild breathing problems that may worsen and cause serious illness and even death.