|
|
|
In 1844, Charles Goodyear obtained the first patent for a rubber condom.
More than 30% of American adults, and about 12% of children utilize health care approaches that were developed outside of conventional medicine.
The use of salicylates dates back 2,500 years to Hippocrates’s recommendation of willow bark (from which a salicylate is derived) as an aid to the pains of childbirth. However, overdosage of salicylates can harm body fluids, electrolytes, the CNS, the GI tract, the ears, the lungs, the blood, the liver, and the kidneys and cause coma or death.
There are over 65,000 known species of protozoa. About 10,000 species are parasitic.
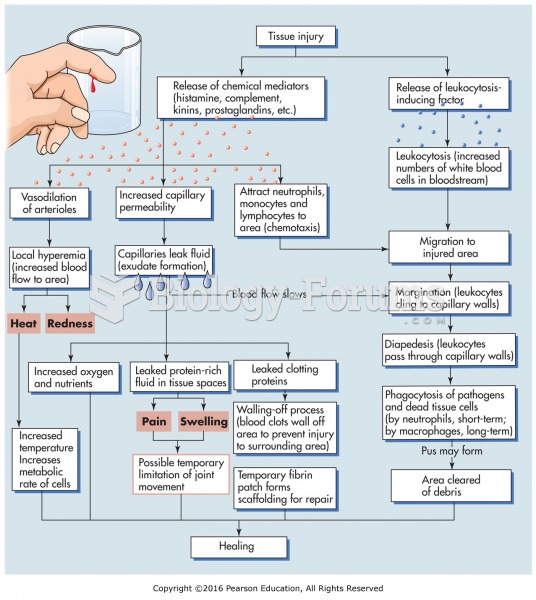
Multiple experimental evidences have confirmed that at the molecular level, cancer is caused by lesions in cellular DNA.