This topic contains a solution. Click here to go to the answer
|
|
|
Did you know?
The types of cancer that alpha interferons are used to treat include hairy cell leukemia, melanoma, follicular non-Hodgkin's lymphoma, and AIDS-related Kaposi's sarcoma.
Did you know?
The human body produces and destroys 15 million blood cells every second.
Did you know?
Approximately one in three babies in the United States is now delivered by cesarean section. The number of cesarean sections in the United States has risen 46% since 1996.
Did you know?
Alcohol acts as a diuretic. Eight ounces of water is needed to metabolize just 1 ounce of alcohol.
Did you know?
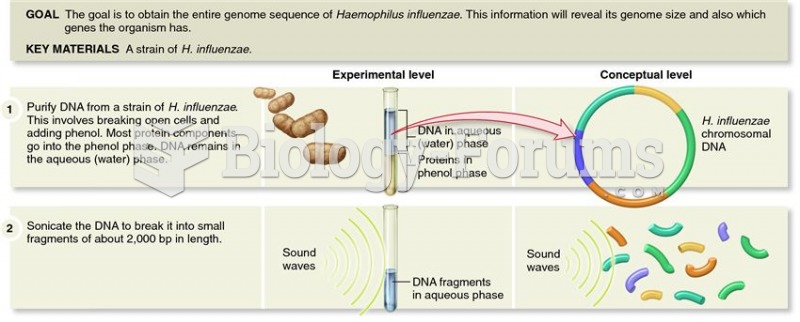
Since 1988, the CDC has reported a 99% reduction in bacterial meningitis caused by Haemophilus influenzae, due to the introduction of the vaccine against it.