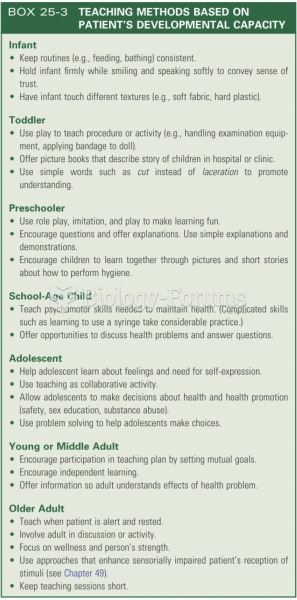
|
|
|
ACTH levels are normally highest in the early morning (between 6 and 8 A.M.) and lowest in the evening (between 6 and 11 P.M.). Therefore, a doctor who suspects abnormal levels looks for low ACTH in the morning and high ACTH in the evening.
There can actually be a 25-hour time difference between certain locations in the world. The International Date Line passes between the islands of Samoa and American Samoa. It is not a straight line, but "zig-zags" around various island chains. Therefore, Samoa and nearby islands have one date, while American Samoa and nearby islands are one day behind. Daylight saving time is used in some islands, but not in others—further shifting the hours out of sync with natural time.
The human body produces and destroys 15 million blood cells every second.
Patients should never assume they are being given the appropriate drugs. They should make sure they know which drugs are being prescribed, and always double-check that the drugs received match the prescription.
Alzheimer's disease affects only about 10% of people older than 65 years of age. Most forms of decreased mental function and dementia are caused by disuse (letting the mind get lazy).