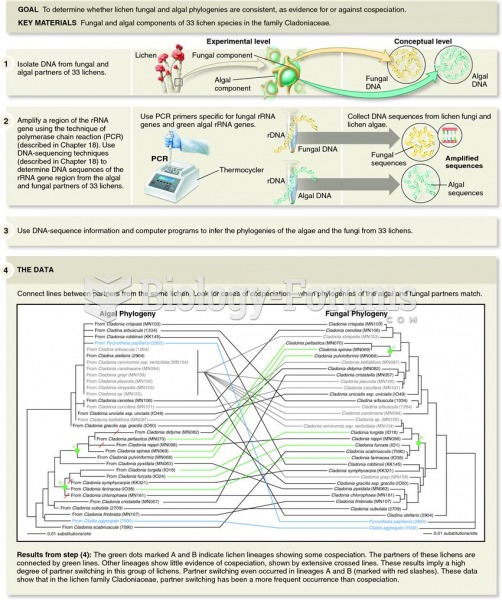
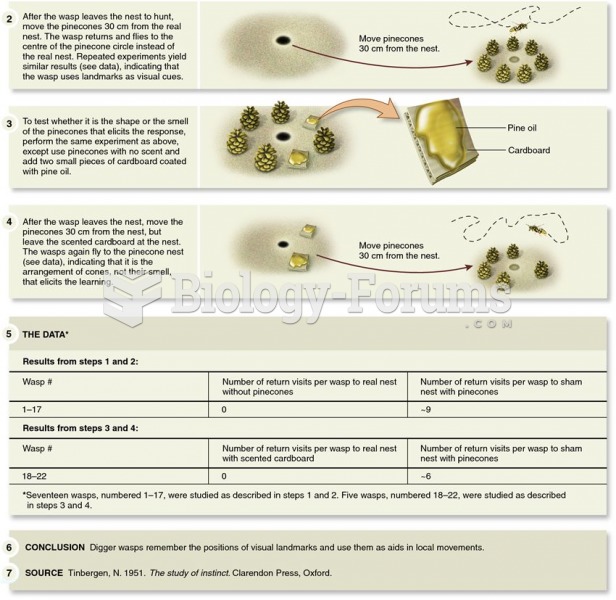
|
|
|
Normal urine is sterile. It contains fluids, salts, and waste products. It is free of bacteria, viruses, and fungi.
Complications of influenza include: bacterial pneumonia, ear and sinus infections, dehydration, and worsening of chronic conditions such as asthma, congestive heart failure, or diabetes.
Chronic marijuana use can damage the white blood cells and reduce the immune system's ability to respond to disease by as much as 40%. Without a strong immune system, the body is vulnerable to all kinds of degenerative and infectious diseases.
The first war in which wide-scale use of anesthetics occurred was the Civil War, and 80% of all wounds were in the extremities.
Your chance of developing a kidney stone is 1 in 10. In recent years, approximately 3.7 million people in the United States were diagnosed with a kidney disease.