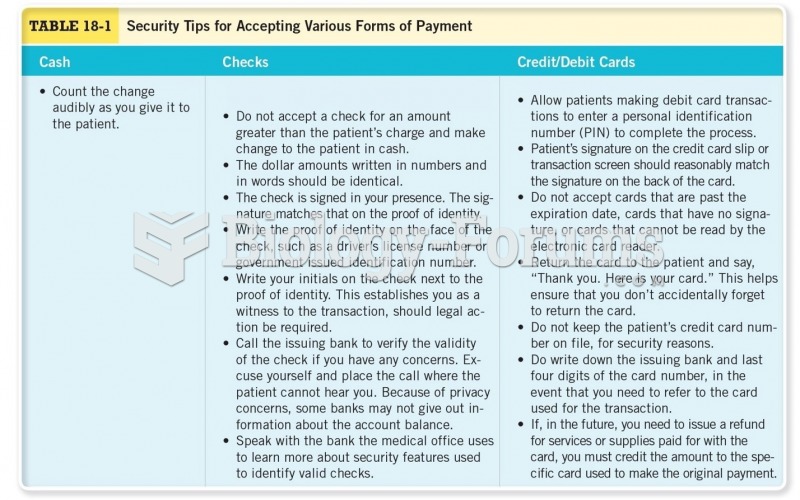
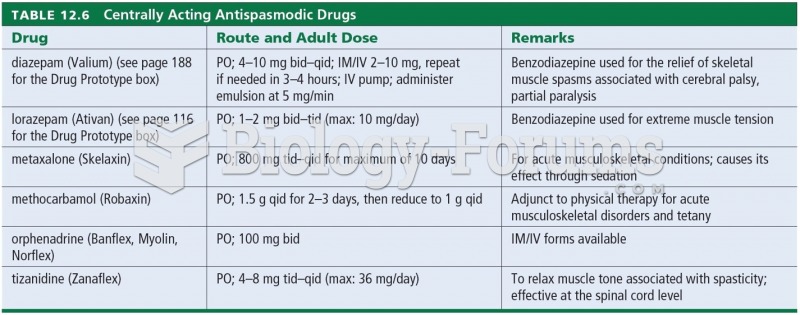
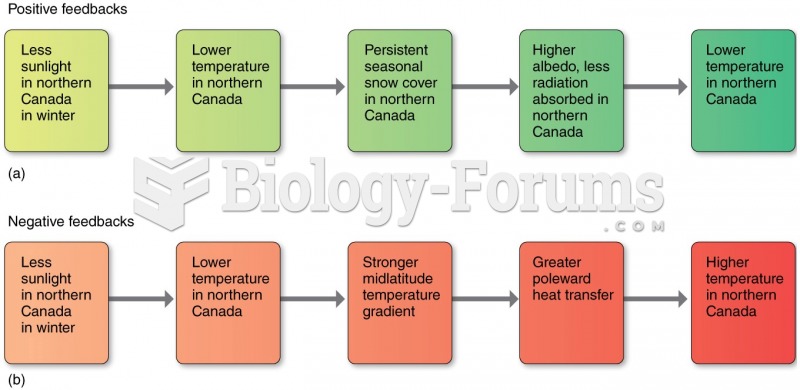
|
|
|
Did you know?
Drying your hands with a paper towel will reduce the bacterial count on your hands by 45–60%.
Did you know?
Since 1988, the CDC has reported a 99% reduction in bacterial meningitis caused by Haemophilus influenzae, due to the introduction of the vaccine against it.
Did you know?
For pediatric patients, intravenous fluids are the most commonly cited products involved in medication errors that are reported to the USP.
Did you know?
Congestive heart failure is a serious disorder that carries a reduced life expectancy. Heart failure is usually a chronic illness, and it may worsen with infection or other physical stressors.
Did you know?
Approximately one in four people diagnosed with diabetes will develop foot problems. Of these, about one-third will require lower extremity amputation.