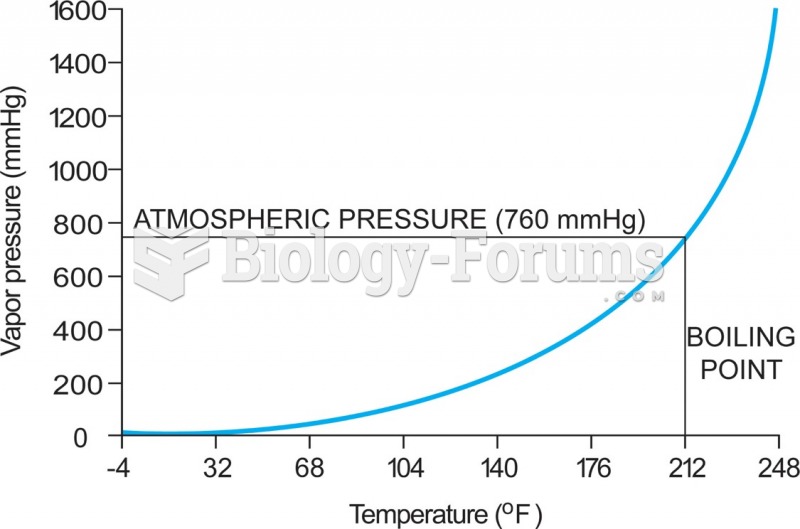
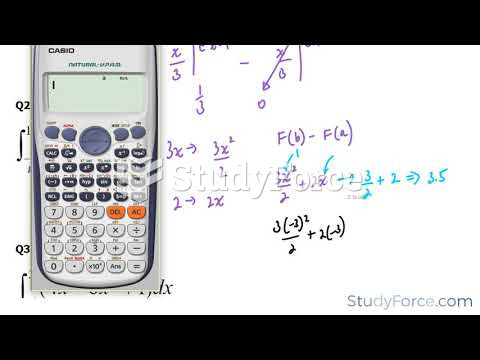
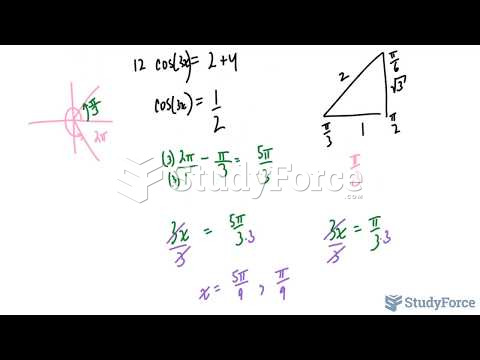
|
|
|
Intradermal injections are somewhat difficult to correctly administer because the skin layers are so thin that it is easy to accidentally punch through to the deeper subcutaneous layer.
Cucumber slices relieve headaches by tightening blood vessels, reducing blood flow to the area, and relieving pressure.
Automated pill dispensing systems have alarms to alert patients when the correct dosing time has arrived. Most systems work with many varieties of medications, so patients who are taking a variety of drugs can still be in control of their dose regimen.
When blood is deoxygenated and flowing back to the heart through the veins, it is dark reddish-blue in color. Blood in the arteries that is oxygenated and flowing out to the body is bright red. Whereas arterial blood comes out in spurts, venous blood flows.
The Romans did not use numerals to indicate fractions but instead used words to indicate parts of a whole.