|
|
|
There are immediate benefits of chiropractic adjustments that are visible via magnetic resonance imaging (MRI). It shows that spinal manipulation therapy is effective in decreasing pain and increasing the gaps between the vertebrae, reducing pressure that leads to pain.
More than 2,500 barbiturates have been synthesized. At the height of their popularity, about 50 were marketed for human use.
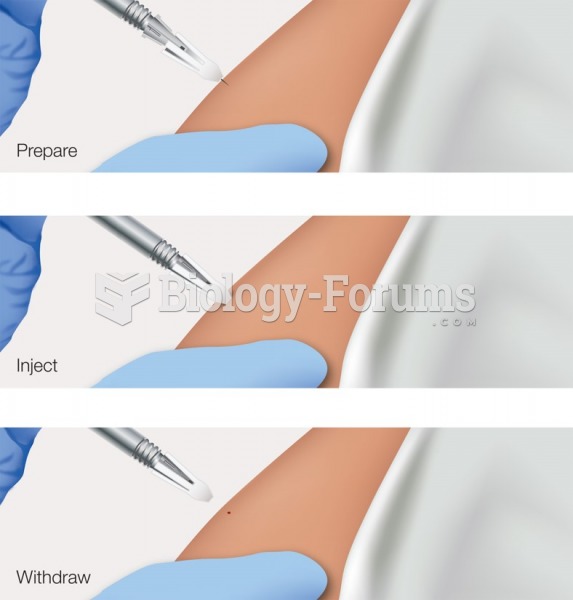
Intradermal injections are somewhat difficult to correctly administer because the skin layers are so thin that it is easy to accidentally punch through to the deeper subcutaneous layer.
Excessive alcohol use costs the country approximately $235 billion every year.
Common abbreviations that cause medication errors include U (unit), mg (milligram), QD (every day), SC (subcutaneous), TIW (three times per week), D/C (discharge or discontinue), HS (at bedtime or "hours of sleep"), cc (cubic centimeters), and AU (each ear).