This topic contains a solution. Click here to go to the answer
|
|
|
Did you know?
The horizontal fraction bar was introduced by the Arabs.
Did you know?
Congestive heart failure is a serious disorder that carries a reduced life expectancy. Heart failure is usually a chronic illness, and it may worsen with infection or other physical stressors.
Did you know?
After a vasectomy, it takes about 12 ejaculations to clear out sperm that were already beyond the blocked area.
Did you know?
Drug-induced pharmacodynamic effects manifested in older adults include drug-induced renal toxicity, which can be a major factor when these adults are experiencing other kidney problems.
Did you know?
The calories found in one piece of cherry cheesecake could light a 60-watt light bulb for 1.5 hours.
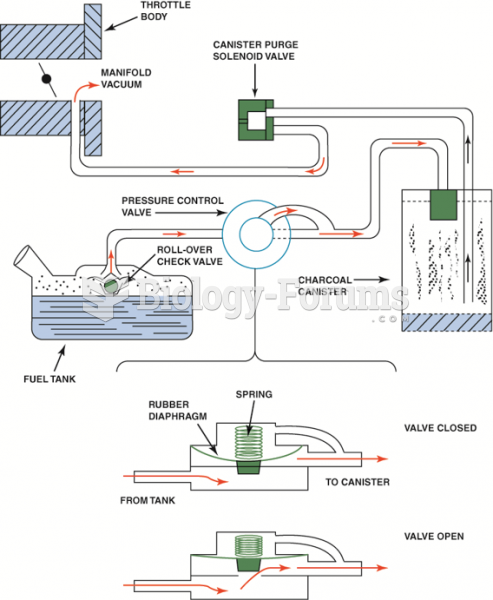 A typical evaporative emission control system. Note that when the computer turns on the canister ...
A typical evaporative emission control system. Note that when the computer turns on the canister ...
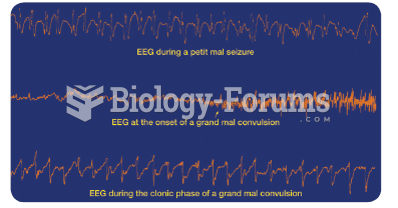 Cortical EEG recorded during epileptic attacks. Notice that each trace is characterized by epileptic ...
Cortical EEG recorded during epileptic attacks. Notice that each trace is characterized by epileptic ...