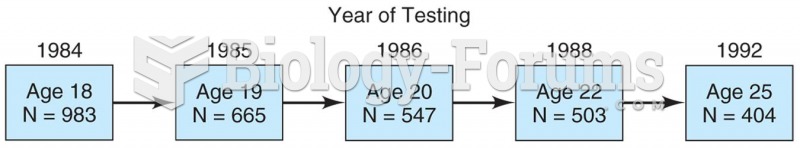
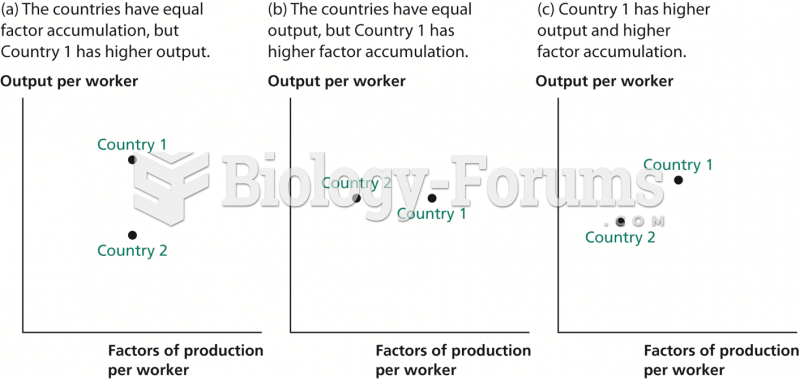
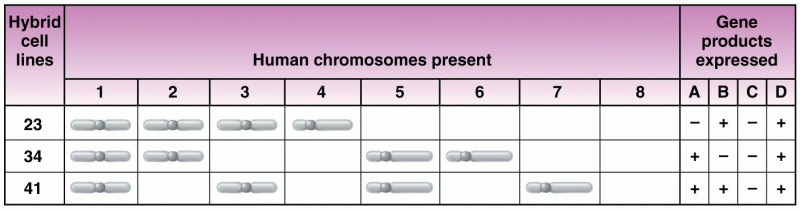
|
|
|
A cataract is a clouding of the eyes' natural lens. As we age, some clouding of the lens may occur. The first sign of a cataract is usually blurry vision. Although glasses and other visual aids may at first help a person with cataracts, surgery may become inevitable. Cataract surgery is very successful in restoring vision, and it is the most frequently performed surgery in the United States.
Always store hazardous household chemicals in their original containers out of reach of children. These include bleach, paint, strippers and products containing turpentine, garden chemicals, oven cleaners, fondue fuels, nail polish, and nail polish remover.
Cancer has been around as long as humankind, but only in the second half of the twentieth century did the number of cancer cases explode.
The strongest synthetic topical retinoid drug available, tazarotene, is used to treat sun-damaged skin, acne, and psoriasis.
Atropine, along with scopolamine and hyoscyamine, is found in the Datura stramonium plant, which gives hallucinogenic effects and is also known as locoweed.