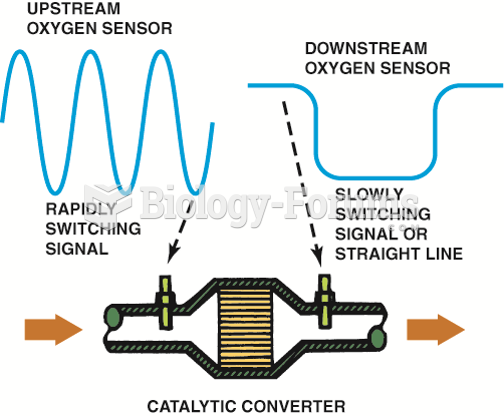
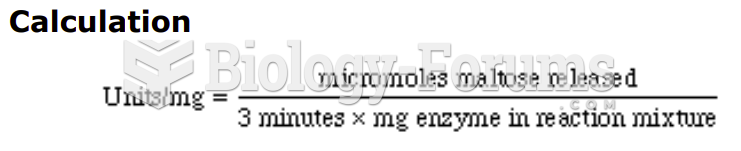|
|
|
Prostaglandins were first isolated from human semen in Sweden in the 1930s. They were so named because the researcher thought that they came from the prostate gland. In fact, prostaglandins exist and are synthesized in almost every cell of the body.
Pope Sylvester II tried to introduce Arabic numbers into Europe between the years 999 and 1003, but their use did not catch on for a few more centuries, and Roman numerals continued to be the primary number system.
Common abbreviations that cause medication errors include U (unit), mg (milligram), QD (every day), SC (subcutaneous), TIW (three times per week), D/C (discharge or discontinue), HS (at bedtime or "hours of sleep"), cc (cubic centimeters), and AU (each ear).
The lipid bilayer is made of phospholipids. They are arranged in a double layer because one of their ends is attracted to water while the other is repelled by water.
Signs and symptoms of a drug overdose include losing consciousness, fever or sweating, breathing problems, abnormal pulse, and changes in skin color.
 In most ecosystems, sunlight provides the ultimate source of energy to power all biological activity
In most ecosystems, sunlight provides the ultimate source of energy to power all biological activity
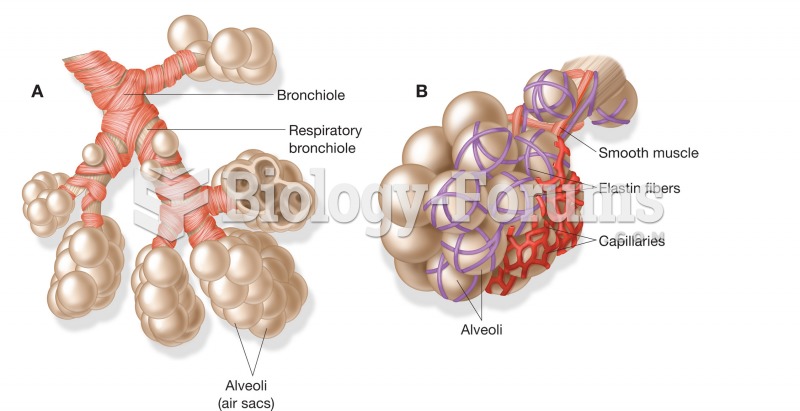 (A) Each bronchiole terminates in an alveolar sac, a group of alveoli; (B) alveoli encased by networ
(A) Each bronchiole terminates in an alveolar sac, a group of alveoli; (B) alveoli encased by networ